
Insights
Zero Auth to Admin: Exploiting Known Vulnerabilites in Real World Pen Tetsts

Krystian Działowy
August 8, 2025
This vulnerability is particularly dangerous due to its low complexity and high impact - it allows complete device takeover with just network access to the Winbox service. About the Vulnerability CVE-2018-14847 is a path traversal vulnerability in the Winbox protocol parser. It allows unauthenticated users to request and download the user database (user.dat) from the router's file system. The file contains credential hashes and sometimes even plaintext passwords, depending on the system version. Step-by-Step Exploitation 1. Crafting the Exploit Packet
The PoC exploit available, for example, here: https://github.com/BasuCert/WinboxPoC contains hardcoded binary payloads (a and b arrays), which represent Winbox-formatted packets. These packets are crafted to:
• initiate a connection to the target router (on port 8291 or 206/236),
• abuse the protocol to request sensitive files using a traversal path (../../../../flash/rw/store/user.dat),
• bypass authentication entirely.
This is the key portion:
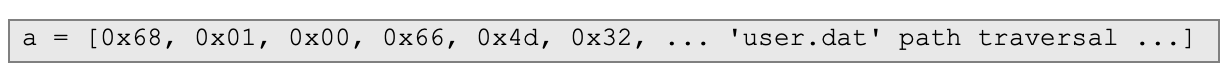 These byte sequences are then transmitted over a raw TCP socket to simulate Winbox protocol behavior.
2. Retrieving Credentials
After sending the packets, the script uses the function dump() from extract_user.py to parse the binary data returned by the router. The credentials (e.g., admin username and password hash or plaintext) are extracted from the user database.
These byte sequences are then transmitted over a raw TCP socket to simulate Winbox protocol behavior.
2. Retrieving Credentials
After sending the packets, the script uses the function dump() from extract_user.py to parse the binary data returned by the router. The credentials (e.g., admin username and password hash or plaintext) are extracted from the user database. Sample execution:
 3. Accessing FTP and GUI
With valid credentials in hand, I’m authenticated to:
3. Accessing FTP and GUI
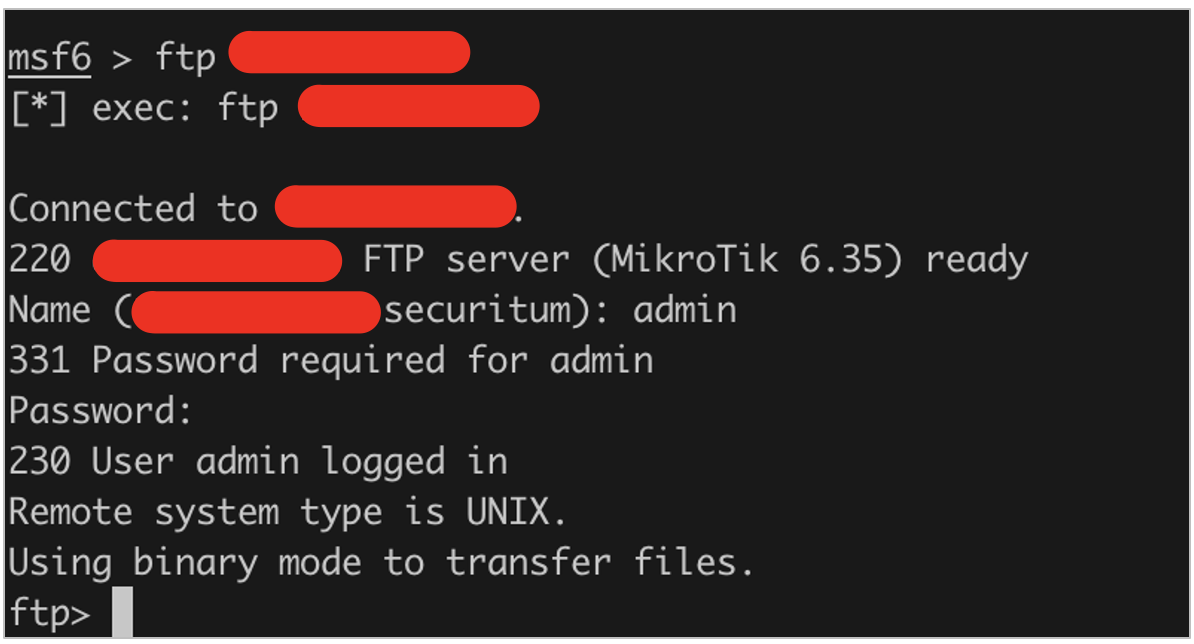
With valid credentials in hand, I’m authenticated to: • the FTP server, gaining access to logs, configs, and the ability to upload/delete files:
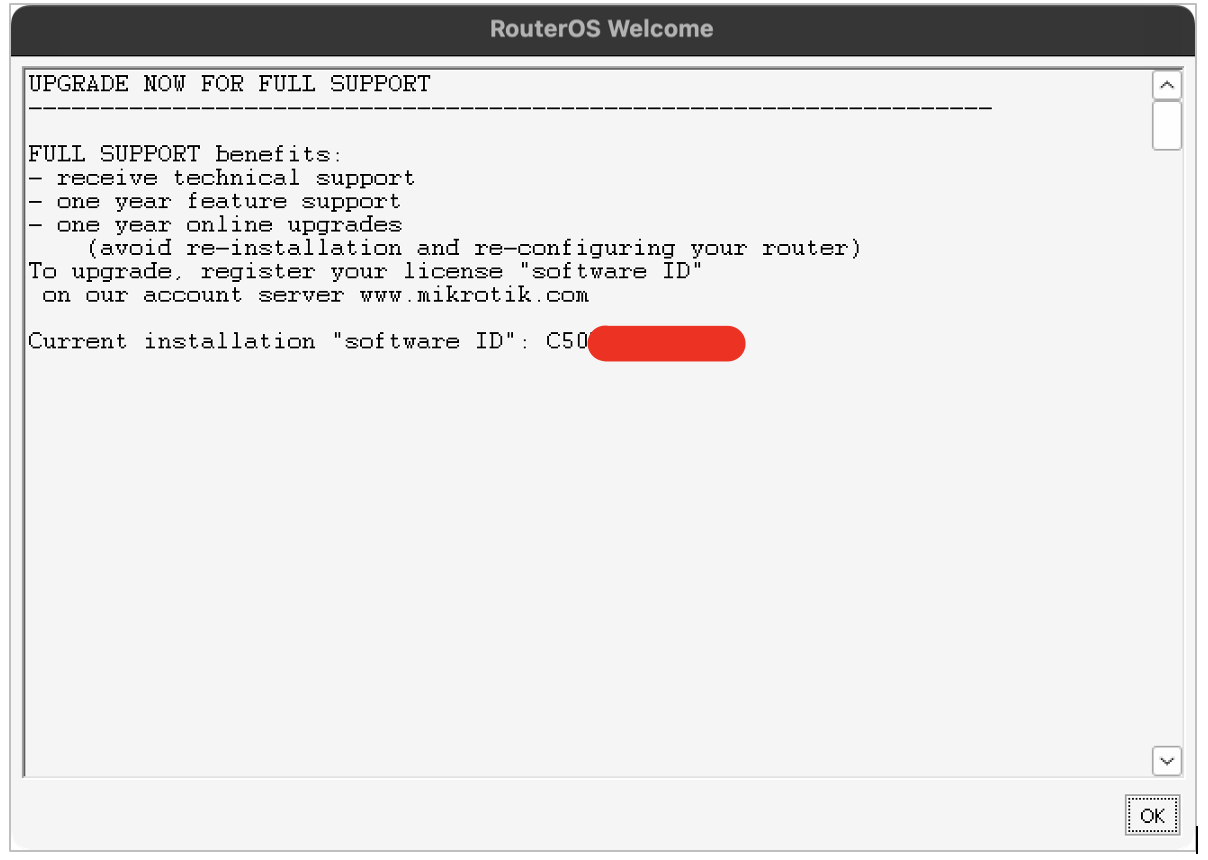
 • the Winbox GUI, where i obtained unrestricted administrative access, where I was greeted at the entrance by such a beautiful message:
• the Winbox GUI, where i obtained unrestricted administrative access, where I was greeted at the entrance by such a beautiful message:
 Final Notes
This case is a textbook example of how one unpatched vulnerability can lead to total infrastructure compromise. Despite being public since 2018, CVE-2018-14847 continues to be exploitable in environments with outdated RouterOS versions.
Final Notes
This case is a textbook example of how one unpatched vulnerability can lead to total infrastructure compromise. Despite being public since 2018, CVE-2018-14847 continues to be exploitable in environments with outdated RouterOS versions. Finally, my recommendations for the client are as follows:
• Immediately upgrade RouterOS to the latest stable version.
• Restrict Winbox and FTP access to trusted IP addresses using firewall rules.
• Change all passwords - assume credentials are compromised.
• Enforce strong password policies, disallowing dictionary passwords and weak passphrases (especially related to the company itself!).
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


