
Insights
Using Malicious Discord Apps to Access User Data Through OAuth2 Permission Grants

Martin Matyja
July 25, 2025
The typical, predictable tactic is to either host content similar to that of the original domain owners or create phishing pages designed to trick users into revealing credentials or downloading malicious software.
In this case, the HTML included only a simple logo and a button. The button redirected users to a Discord OAuth2 invitation link for one of the Discord Apps, specifically, the hosted application created by our actor.
The link looked like this:
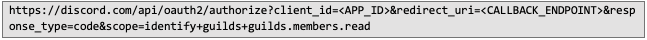 The link directs to Discord’s OAuth2 authorization endpoint. By including the client_id, it specifies which Discord app is requesting access to the user’s data. The redirect_uri parameter defines where the user will be redirected after completing the authorization process. Another key parameter is scope, which outlines the permissions the user grants to the application by clicking the link.
The link directs to Discord’s OAuth2 authorization endpoint. By including the client_id, it specifies which Discord app is requesting access to the user’s data. The redirect_uri parameter defines where the user will be redirected after completing the authorization process. Another key parameter is scope, which outlines the permissions the user grants to the application by clicking the link. This article does not cover subdomain takeover attacks; instead, it focuses on the Discord App. We will explore an intriguing method of collecting user data by creating a Discord App for phishing purposes and analyse the types of data such an app can access.
Discord App overview Discord Apps, also known as Developer Apps, are bots or programs integrated into Discord servers to enhance communities with additional features, tools, and automation. If you use Discord, you’ve likely interacted with one of these apps running on a server you belong to.
These apps use OAuth2 for secure user authentication and permission management, ensuring user credentials remain private. OAuth2 allows users to grant specific access privileges, enabling safe integration of bots and external services while improving security, privacy, and control over connected applications.
Discord App permissions You can configure a variety of permissions that a Discord App can use on behalf of the user who grants access. Let’s look at some of the permissions that can be granted to the app:
• identify – allow to obtain various information about the profile, but without the email address.
Example data object for one of the accounts used during the creation of this article:
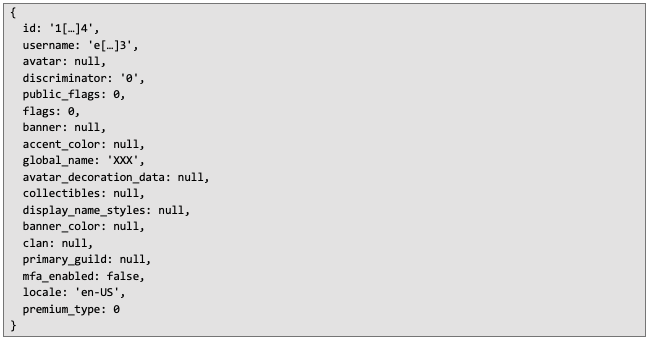 • email – the same as identify but with email address included,
• email – the same as identify but with email address included,• connections - allows to return linked third-party accounts,
• guilds - allows to return basic information about all a user's guilds.
Some permissions require Discord approval and were not tested during the article’s creation. However, they present additional potential methods to gain broader access to a victim’s data. Examples of notable permissions include:
• dm_channels.read - allows app to see information about the user's DMs and group DMs
• applications.builds.upload - allows app to upload/update builds for a user's applications
• relationships.read - allows app to know a user's friends and implicit relationships
Example scenario Let’s create a simple app that impersonates the brand with little modification - Sékurak. To increase trust, the app includes a logo generated by one of the most popular LLMs:
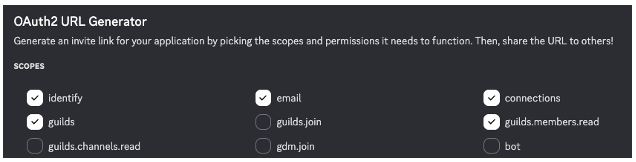
 The next step is to specify the permissions our Discord app will request from the user.
The next step is to specify the permissions our Discord app will request from the user.
 Discord will then generate a URL structured like the example shown at the beginning of the article. When the user enters this URL in their browser, they will be redirected to a Discord page containing a form to authorize the app to access the specified account permissions.
Discord will then generate a URL structured like the example shown at the beginning of the article. When the user enters this URL in their browser, they will be redirected to a Discord page containing a form to authorize the app to access the specified account permissions.
 The bottom section of the form also reveals some information about the Discord app:
The bottom section of the form also reveals some information about the Discord app:
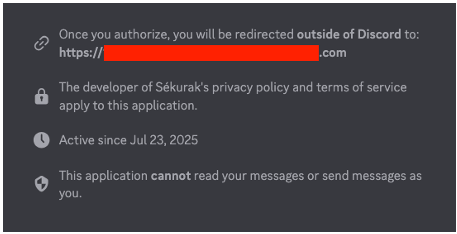 Let’s be honest, it’s hard to overlook the information about the permissions an app requests. Discord presents this information transparently, helping users clearly understand the permissions they’re granting. It’s a great approach!
Let’s be honest, it’s hard to overlook the information about the permissions an app requests. Discord presents this information transparently, helping users clearly understand the permissions they’re granting. It’s a great approach! Therefore, the burden of phishing persuasion should be shifted to the source of the link granting permissions, i.e., the HTML code, logo and app name.
When the user clicks the “Authorize” button, access is granted, and they are redirected to the previously specified URL with code value:
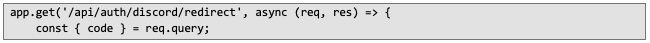
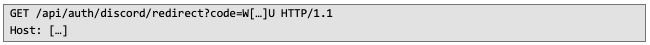 Let's review a basic HTTP server with a redirection handler using the Express framework. Below is the endpoint handler:
Let's review a basic HTTP server with a redirection handler using the Express framework. Below is the endpoint handler:
 To obtain an access token, we need to send a request to the appropriate endpoint using our code value (typical OAuth2 authorization code flow).
To obtain an access token, we need to send a request to the appropriate endpoint using our code value (typical OAuth2 authorization code flow).
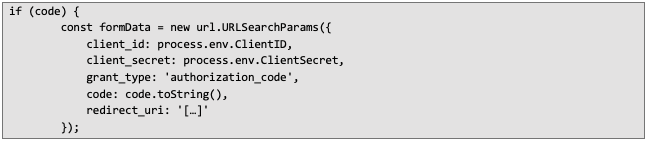 Obtaining access token to access Discord API latter:
Obtaining access token to access Discord API latter:
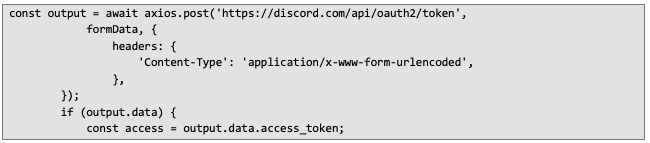 Response from the request above:
Response from the request above:
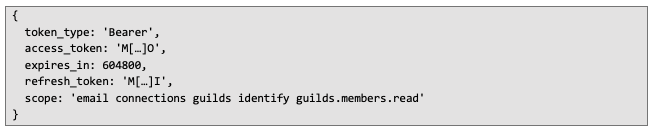 Now that we have an access token, we can request data from the Discord API on behalf of the user.
Now that we have an access token, we can request data from the Discord API on behalf of the user. To retrieve the user's profile data, send a request to the /users/@me endpoint:
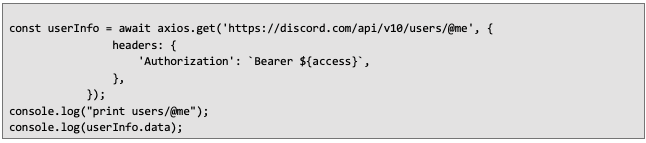 Example response of the user data:
Example response of the user data:
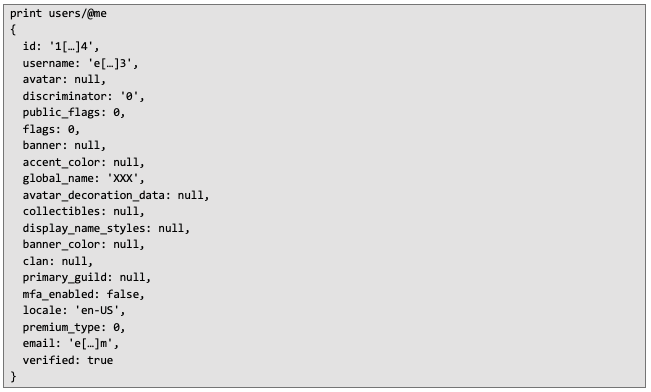 Another example is retrieving information about the Discord guilds (servers) the user belongs to, which can be done as follows:
Another example is retrieving information about the Discord guilds (servers) the user belongs to, which can be done as follows:
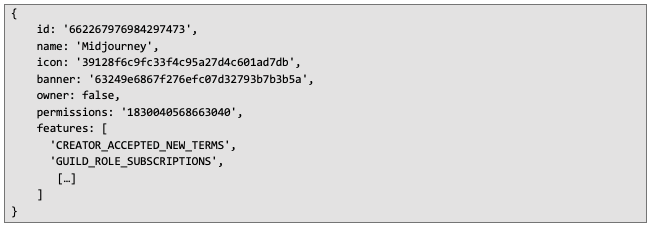
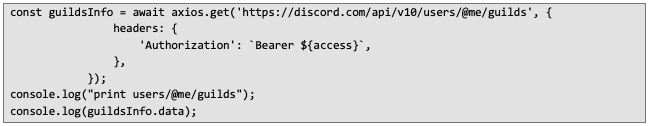 Example response showing membership in the Midjourney server:
Example response showing membership in the Midjourney server:
 Conclusion
This article shows a simple method to create an application that may attempt to access user data on the platform. Since Discord openly displays user permissions, it’s possible to impersonate any “app identity,” such as a well-known brand. This impersonation can greatly improve the chances of gaining access, especially when combined with social engineering tactics like offering a “free voucher for a certificate” through the Discord app.
Conclusion
This article shows a simple method to create an application that may attempt to access user data on the platform. Since Discord openly displays user permissions, it’s possible to impersonate any “app identity,” such as a well-known brand. This impersonation can greatly improve the chances of gaining access, especially when combined with social engineering tactics like offering a “free voucher for a certificate” through the Discord app. To protect your data, follow these guidelines:
- Always review the permissions the Discord app is requesting.
- Verify the app’s authenticity and confirm it’s from the creator you trust.
- If you don’t need the app, avoid using it and don’t grant any permissions.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


