
Insights
How a simple lack of SMS code verification can compromise financial security?

Securitum
April 30, 2024
What happened?
During audits, it's crucial to check all possible attack vectors, even the seemingly obvious functionalities. This diligence led us to discover, during one of our web application audits, that the server does not verify the correctness of the SMS code used by applicants during the credit request process, either at the start or at the final document signing stage. In short: a credit application without any verification.
In this case, to submit a credit application, one only needed to know the client's national identification number.
How does the attack proceed?
Logging into the client portal requires the national identification number. After entering it, SMS code authentication follows. Upon entering the code, the following request is sent:
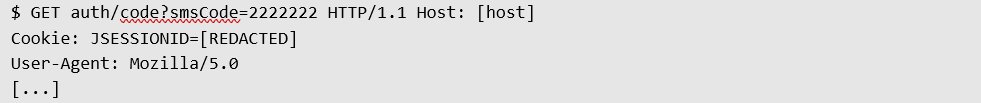
The server does not check the correctness of the entered SMS code; it only needs to be six digits long to grant authorization:

Below is a list of example codes that worked during our tests:
222222
333333
123456
987321
Furthermore, it was confirmed that at the end of the process—during the user’s signing of the completed document with consents, the application requests another SMS code. However, in this case, the code is not even sent to the server in the GET request!
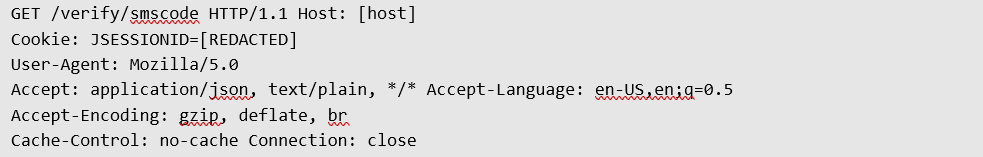
Despite this, the process concludes successfully, and we are informed that the credit application has been submitted.
What can we recommend?
During application development, remember to ensure that all implemented authentication mechanisms are always verified on the server side.
#Cybersecurity #RaceCondition #WebSecurity #Pentesting #RealWorldPentests
Other Insights

Helping secure DOMPurify
MICHAŁ BENTKOWSKI
December 21, 2020
Within last year I shared a a few writeups of my bypasses of HTML sanitizers, including: > Write-up of DOMPurify 2.0.0 bypass using mutation XSS > Mutation XSS via namespace confusion – DOMPurify < 2.0.17 bypass While breaking sanitizers is fun and I thoroughly enjoy doing it, I reached a point where I began to think whether I can contribute even more and propose a fix that will kill an entire class of bypasses.

Pyscript - or rather Python in your browser + what can be done with it
Michał Bentkowski
September 10, 2022
A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in the browser is not new; the pyodide project has allowed this for a long time...

Art of bug bounty a way from JS file analysis to XSS
jAKUB żOCZEK
July 1, 2020
Summary: During my research on other bug bounty program I've found Cross-Site Scripting vulnerability in cmp3p.js file, which allows attacker to execute arbitrary javascript code in context of domain that include mentioned script. Below you can find the way of finding bug bounty vulnerabilities from the beginning to the ...


