
Pentest Chronicles
Possible Misconfigurations in Active Directory – Security Audit Findings

Jarosław Kamiński
February 28, 2025
During an Active Directory security audit, a number of potential misconfigurations and security vulnerabilities were identified. If left unaddressed, these issues could increase the attack surface, making the domain susceptible to exploitation by malicious actors, both internal and external. Case #1: Any User Can Log into the RDP Service An analysis of Active Directory revealed that any user belonging to the "Domain Users" group can log into the RDP service on the three workstations listed below. It is necessary to verify whether these access permissions should be maintained in their current form.
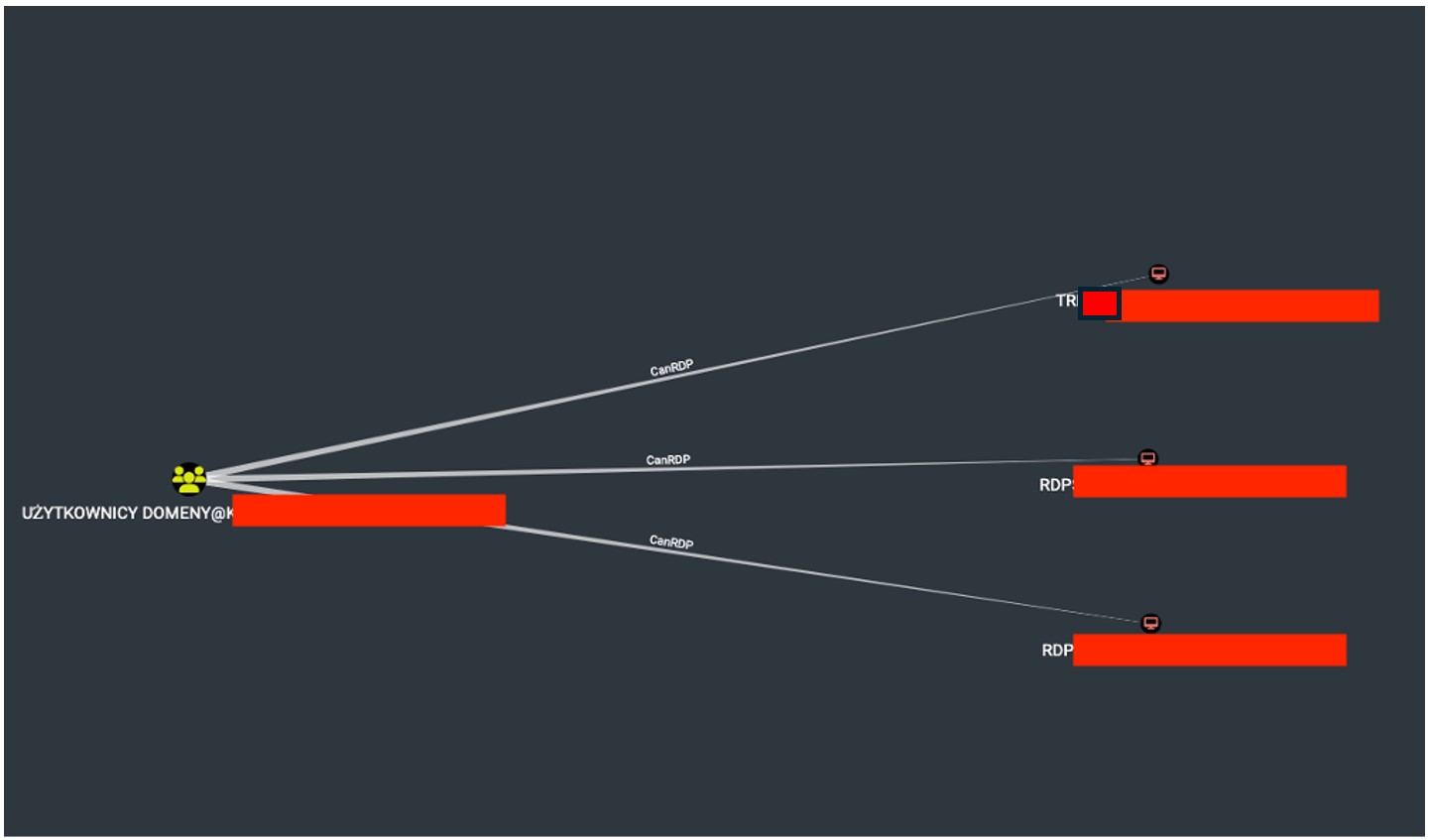 The Screenshot presents a view from the BloodHound software, indicating that members of the "Domain Users" group have the ability to connect to the three workstations shown in the image.
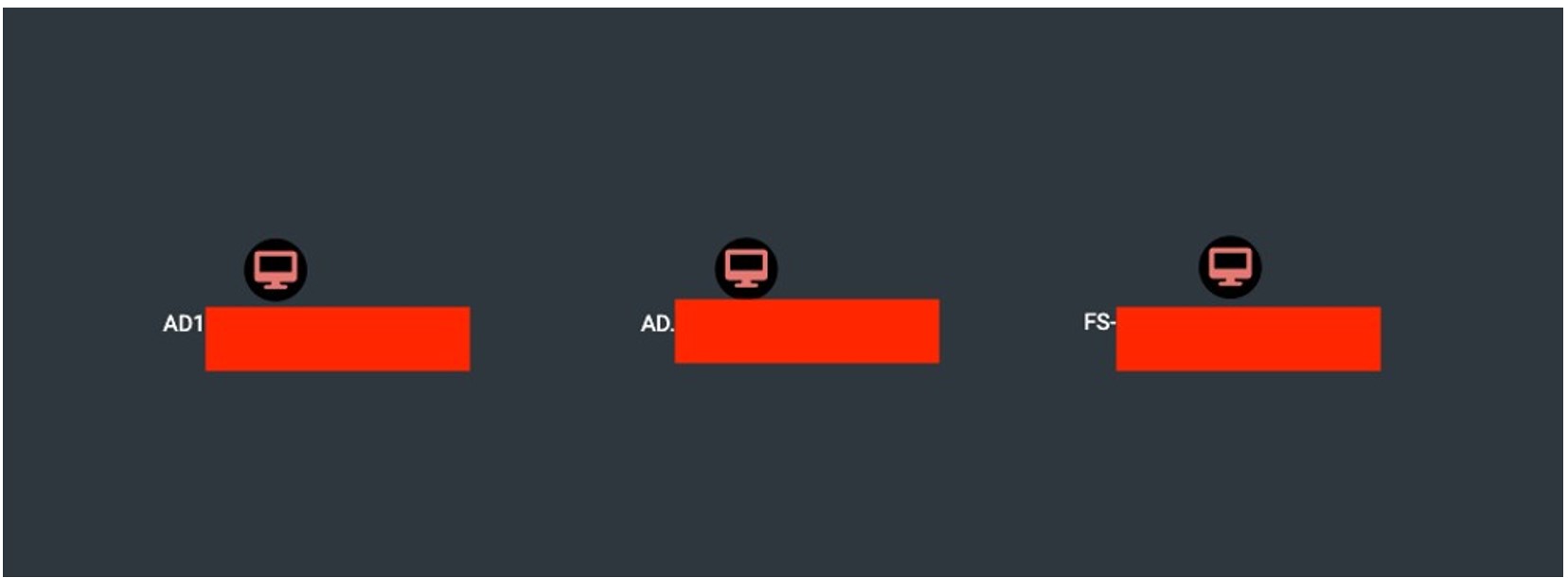
The Screenshot presents a view from the BloodHound software, indicating that members of the "Domain Users" group have the ability to connect to the three workstations shown in the image. 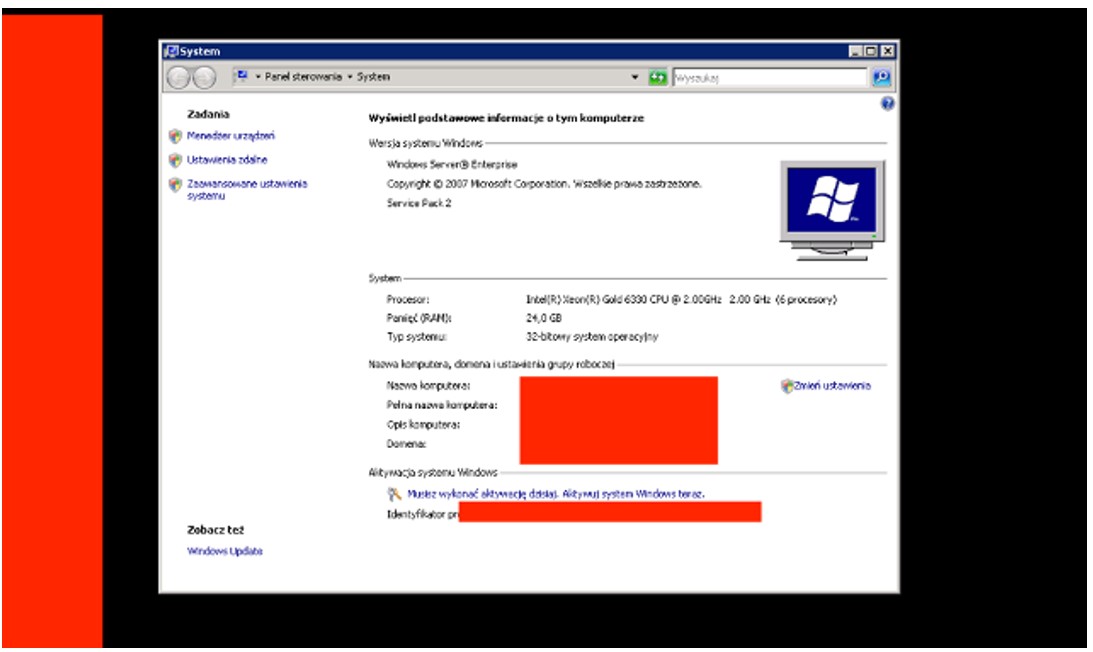 The screenshot shows the view after logging into the workstation using the RDP service. Case #2: Unconstrained Delegation Three computers have been detected with the "Trust this computer for delegation to any service" option enabled. If one of these computers is compromised, this setting allows for privilege escalation by impersonating any user within the domain.
The screenshot shows the view after logging into the workstation using the RDP service. Case #2: Unconstrained Delegation Three computers have been detected with the "Trust this computer for delegation to any service" option enabled. If one of these computers is compromised, this setting allows for privilege escalation by impersonating any user within the domain.Understandably, the computers named AD1.XXX and AD.XXX may support this configuration due to their roles. However, it is necessary to verify the reason why the workstation named FSXXX.XXX has also been configured this way.
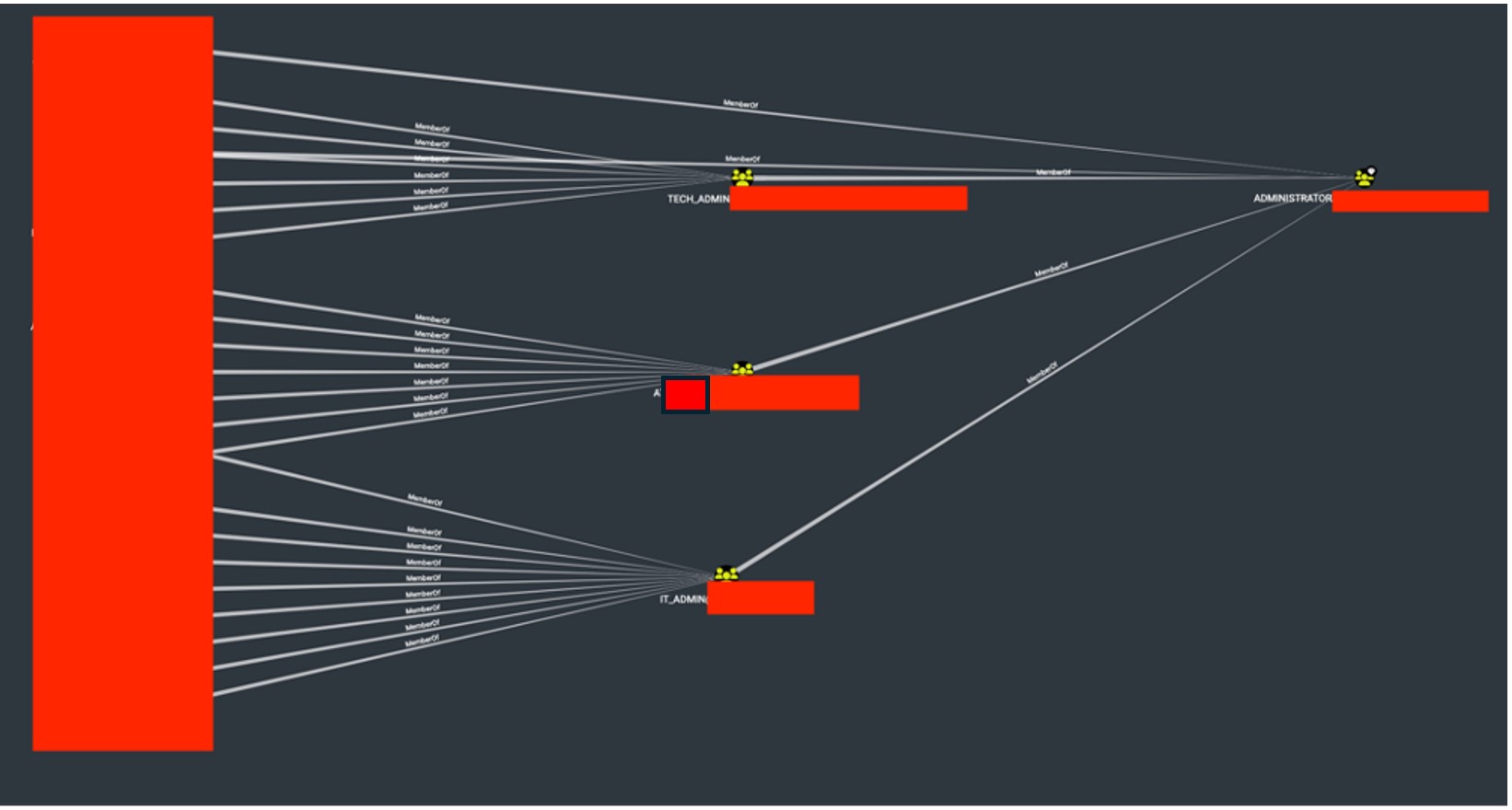
 Case #3: A Very Large Number of Administrative Accounts The audit detected a significant number of accounts with administrative privileges. The list includes both personal accounts and purely technical accounts.
Case #3: A Very Large Number of Administrative Accounts The audit detected a significant number of accounts with administrative privileges. The list includes both personal accounts and purely technical accounts. A high number of accounts with administrative privileges increases the attack surface on the AD controller. It is necessary to verify whether all users should have such broad access to the AD controller.
 Case #4: GPO Abuse The audit detected accounts with the ability to manage specific GPO policies. This configuration could ultimately lead to the takeover of the AD controller.
Case #4: GPO Abuse The audit detected accounts with the ability to manage specific GPO policies. This configuration could ultimately lead to the takeover of the AD controller. It is necessary to verify the legitimacy of these accounts having permission to edit the listed policies.
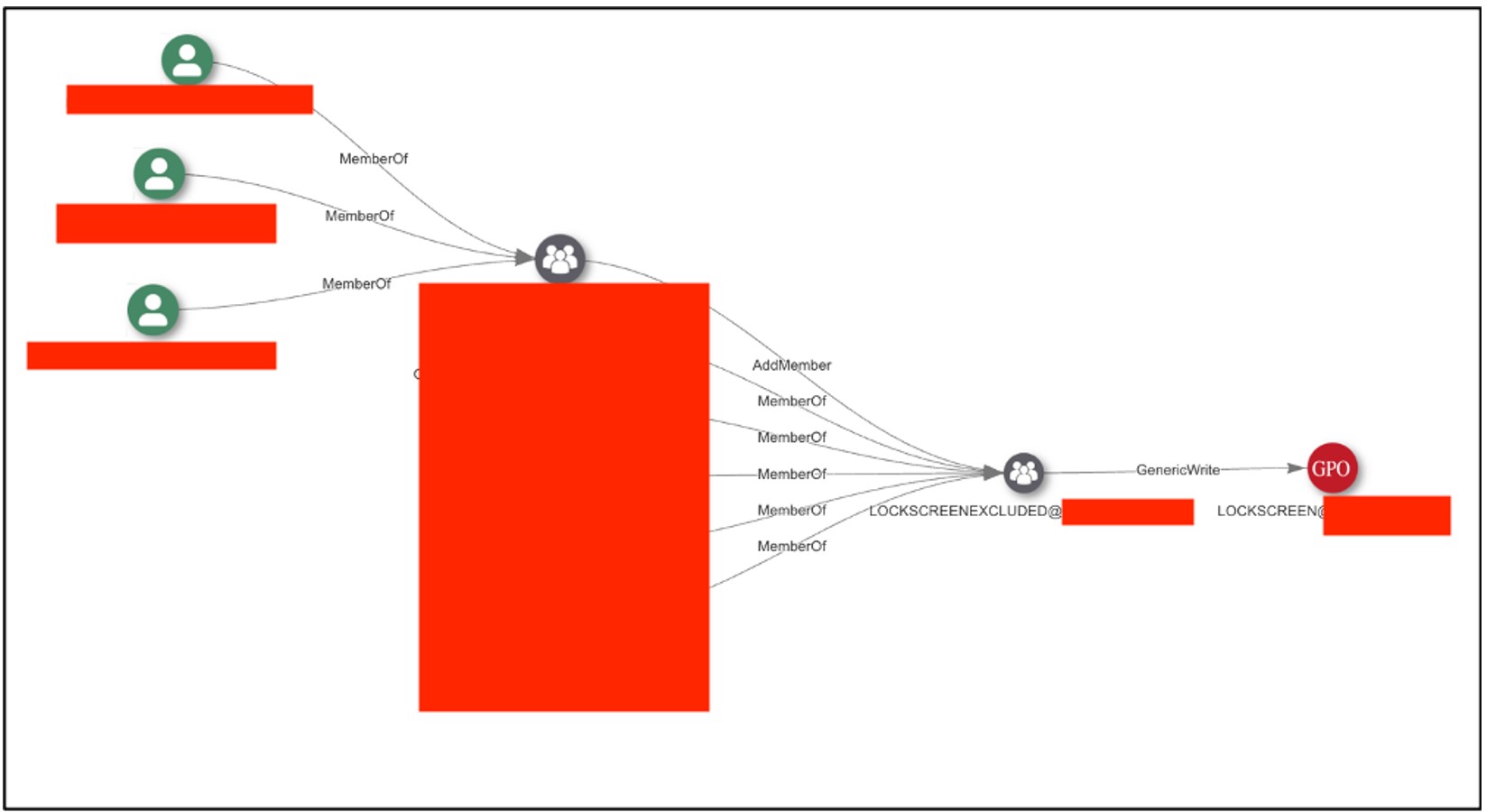 The screenshot shows a view from the AD Miner tool, highlighting the path leading to the editing of the GPO LOCKSCREEN@XXXX policy.
The screenshot shows a view from the AD Miner tool, highlighting the path leading to the editing of the GPO LOCKSCREEN@XXXX policy.The list of accounts with permission to edit this policy includes, among others, RECEPTION! Case #5: Users Can Connect to AD Controllers via RDP During the audit, 135 users were identified as having the ability to connect to AD controllers using the RDP service.
It is urgently recommended to verify whether these users actually have this access and then assess the necessity of such a configuration.
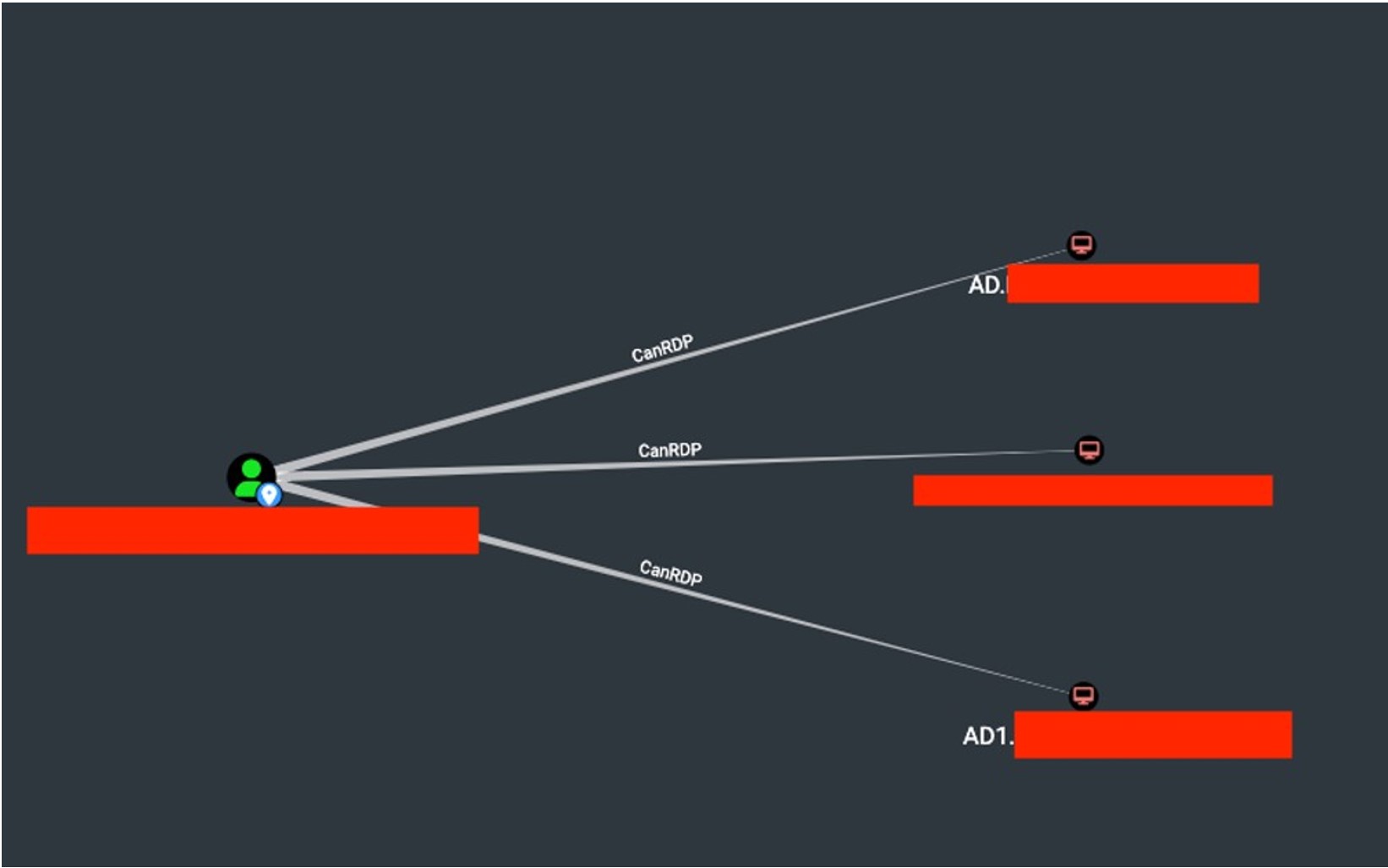 The screenshot shows a view from the BloodHound application, highlighting the possible RDP connections for the user XXXXX. Case #6: User with DCSync Execution Ability on the AD Controller During the audit, the user SQL3.ADMIN was identified as having the ability to perform DCSync (a form of "replication" of the controller) on the AD controller.
The screenshot shows a view from the BloodHound application, highlighting the possible RDP connections for the user XXXXX. Case #6: User with DCSync Execution Ability on the AD Controller During the audit, the user SQL3.ADMIN was identified as having the ability to perform DCSync (a form of "replication" of the controller) on the AD controller.It is necessary to verify the legitimacy of this configuration.
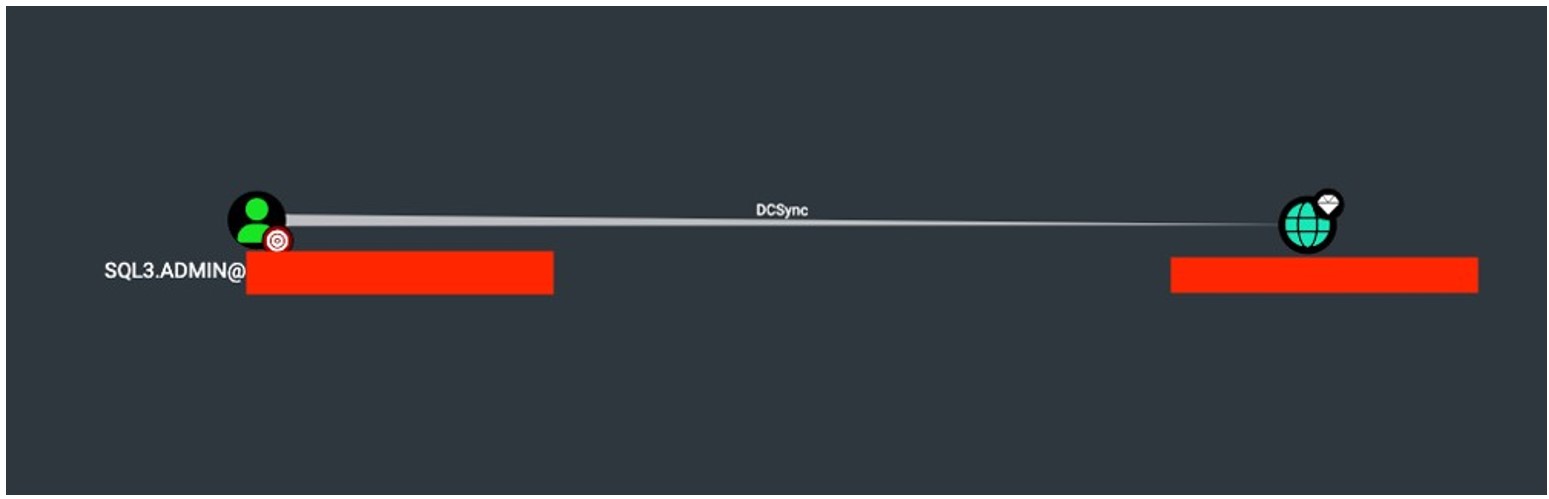 The screenshot shows a view from the BloodHound application, indicating that the user SQL3.ADMIN has the ability to perform DCSync on the AD controller. Case #7: Workstation with Elevated Privileges The workstation APP-TEST has been identified as potentially having excessive privileges, allowing for the modification of GPO policies, which could ultimately lead to an escalation to the AD controller.
The screenshot shows a view from the BloodHound application, indicating that the user SQL3.ADMIN has the ability to perform DCSync on the AD controller. Case #7: Workstation with Elevated Privileges The workstation APP-TEST has been identified as potentially having excessive privileges, allowing for the modification of GPO policies, which could ultimately lead to an escalation to the AD controller. 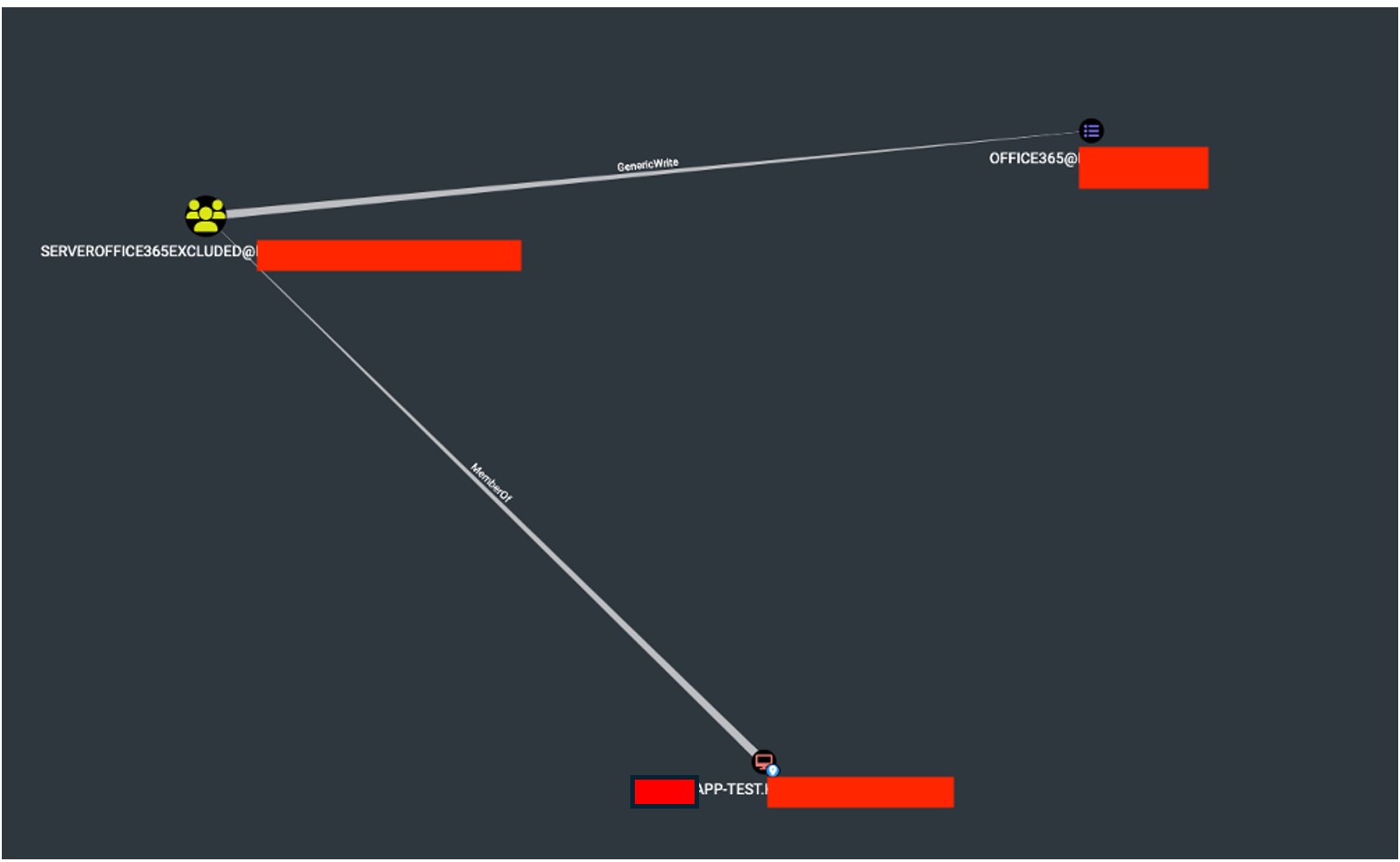 The screenshot shows a view from the BloodHound software, indicating that the APP-TEST workstation belongs to the SERVEROFFICE365EXCLUDED group, which has permission to edit the GPO OFFICE365 policy.
The screenshot shows a view from the BloodHound software, indicating that the APP-TEST workstation belongs to the SERVEROFFICE365EXCLUDED group, which has permission to edit the GPO OFFICE365 policy. 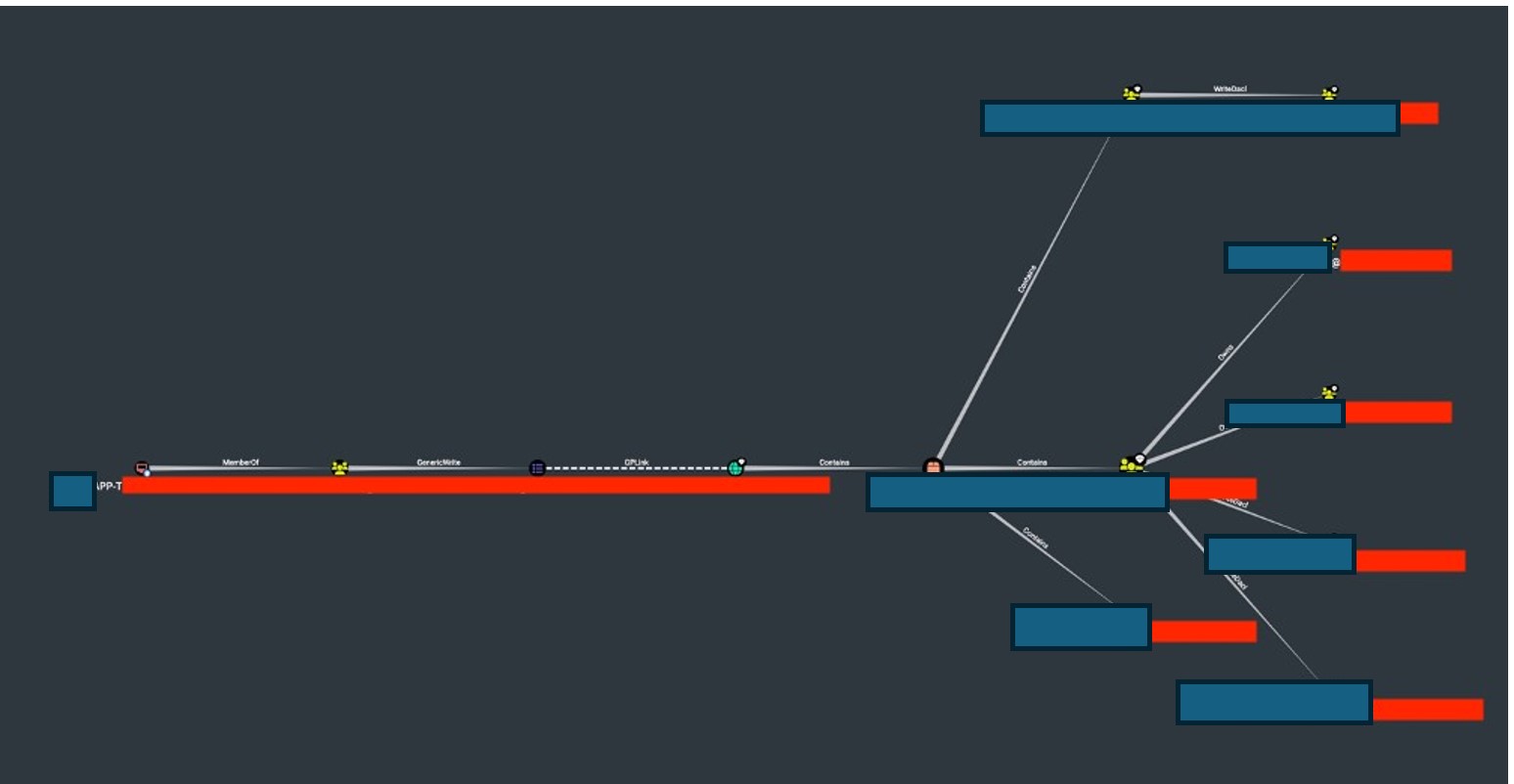 The screenshot shows a view from the BloodHound software, highlighting a possible escalation path for taking over the AD controller using the APP-TEST workstation.
The screenshot shows a view from the BloodHound software, highlighting a possible escalation path for taking over the AD controller using the APP-TEST workstation. Conclusion and Next Steps The audit findings indicate that multiple Active Directory misconfigurations could potentially lead to privilege escalation, domain takeover, or unauthorized access. Each of these cases should be carefully reviewed and mitigated to enhance security posture and reduce risk.
Key Action Points:
• Review RDP access policies and remove unnecessary permissions.
• Restrict Unconstrained Delegation to only critical systems.
• Reduce the number of administrative accounts to minimize the attack surface.
• Audit GPO permissions and limit editing rights to trusted users.
• Restrict DCSync execution to essential accounts only.
• Implement strong password policies, especially for privileged accounts.
By addressing these misconfigurations, the Active Directory environment can be significantly hardened against potential attacks and privilege escalations.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


