
Insights
MAC Spoofing Made Easy: Lessons in LAN and Physical Security from a Real Pentest

Krystian Działowy
July 18, 2025
We tested exactly that scenario, walking into an open conference room and connecting a laptop using a random MAC address. Although the device received a DHCP lease, access to internal resources was blocked, and CrowdStrike EDR registered the connection attempt. However, the story didn’t end there.
Using standard reconnaissance tools, we identified an internal device’s IP and MAC address. After spoofing that MAC and statically configuring the IP, we were granted full access to the internal LAN: undetected and unrestricted.
The client’s assumption was that MAC-based access control or static DHCP/ARP entries would be sufficient protection. We set out to challenge that and what we discovered serious concerns.
The network lacked 802.1X, MAC filtering, segmentation, and physical access controls making it vulnerable to low effort but high impact attacks.
Technical Details Step 1: Plugging in with a random MAC Address
As I mentioned above, we connected a laptop to an Ethernet wall port in a publicly accessible conference room. Using a random, previously unknown MAC address, we received an IP address via DHCP:
 No port level or MAC-based restrictions were observed at the switch level, but ultimately, at this stage we didn’t gain access to any internal systems or resources. As we later found out, CrowdStrike EDR logged and reported the connection attempt, but no one from the client responded or paid attention to us. So, we decided to continue our efforts.
No port level or MAC-based restrictions were observed at the switch level, but ultimately, at this stage we didn’t gain access to any internal systems or resources. As we later found out, CrowdStrike EDR logged and reported the connection attempt, but no one from the client responded or paid attention to us. So, we decided to continue our efforts.
Step 2: Scanning the subnet
Despite the access limitations, we performed passive scanning by netdiscover tool to map MAC/IP pairs in the local subnet:
 Bingo! We discovered a lot of hosts, and we decided to choose the one that looked most promising (we assumed, based on the manufacturer's name, that it might be one of the main servers).
Bingo! We discovered a lot of hosts, and we decided to choose the one that looked most promising (we assumed, based on the manufacturer's name, that it might be one of the main servers).
Step 3: Spoofing and impersonation
All that remains is to disable the existing interface, clone the MAC address, and manually set previously acquired MAC address and static IP address:
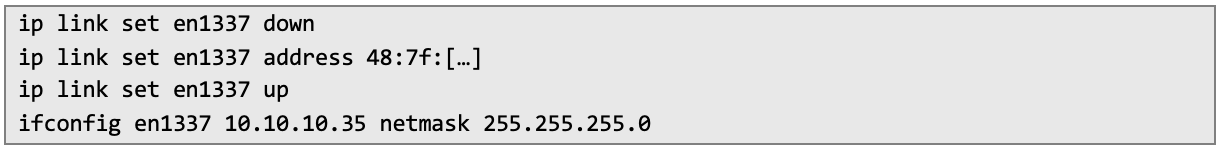 Final Notes This test revealed critical gaps in both logical and physical security:
Final Notes This test revealed critical gaps in both logical and physical security:
• Despite deploying CrowdStrike EDR, the client was vulnerable to basic LAN intrusion tactics.
• The entire office floor lacked access controls, no reception desk or badge-gated zones.
• An attacker could walk in unnoticed, connect a rogue device, and attack the network before anyone reacted.
A skilled attacker could easily split the attack into phases: first scan the network to collect MACs, then return later to impersonate a known device - this time bypassing EDR detection entirely.
To protect against such scenarios, we recommend to our client a layered approach combining physical, network, and endpoint controls.
Physical Security • Implement badge-based access control for sensitive areas, including the IT department and adjacent rooms.
• Install surveillance or reception coverage at entrances, particularly on unguarded office floors.
Network Security • Enforce 802.1X authentication (wired and wireless), requiring valid client certificates or credentials.
• Enable port-level MAC filtering on switches using port security.
• Segment the network using VLANs:
o Separate infrastructure, critical services (e.g. Intranet, billing portals), and user workstations.
o Place admin panels and device management interfaces in isolated VLANs.
Monitoring and Response • Continuously monitor MAC/IP changes and flag duplicates.
• Create alerts for new devices, especially on non-public ports.
• Ensure the EDR system integrates with NAC or SIEM to enable automated incident response.
In conclusion, even well-equipped organisations may fall victim to simple attacks - especially when LAN access is left unguarded. In the end, network security starts not with complex detection but with preventing unauthorised connections in the first place.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


