
Insights
How to extract certificates and private keys from iOS Keychain

Marcin Zięba
September 12, 2025
From a security assessment perspective, understanding how client certificates and private keys are stored in the Keychain is crucial, particularly since these assets often play a key role in authentication flows with backend services. Mismanagement or insufficient protections - especially regarding the application’s resilience - can provide attackers with opportunities on compromised devices. Authentication in iOS Apps: X.509 Client Certificates Many modern iOS applications implement mutual TLS (mTLS) authentication as part of their security design. In this model, the client must not only validate the server’s certificate but also present an X.509 certificate and the associated private key to prove its identity.
Some of them may not fully utilize mTLS and implement only access control based on user’s identity backed by a client certificate.
The client certificate and key are typically stored in the Keychain and accessed by the app whenever a secure session is initiated. If an attacker is able to extract these credentials, they could impersonate a legitimate client, bypassing standard authentication mechanisms. How such information can be extracted? After fulfilling the initial requirements (jailbreak detection and instrumentation prevention), intercepting the application’s traffic through an HTTP proxy may result in additional errors, such as the one shown for the request below:
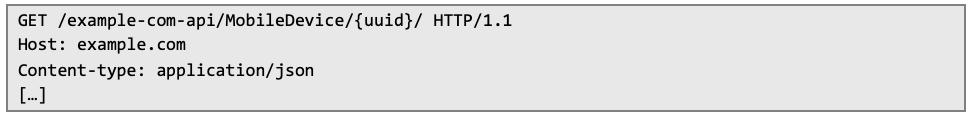 The server’s response displays an error related to the certificate because HTTP proxies are not capable of forwarding certificates:
The server’s response displays an error related to the certificate because HTTP proxies are not capable of forwarding certificates:
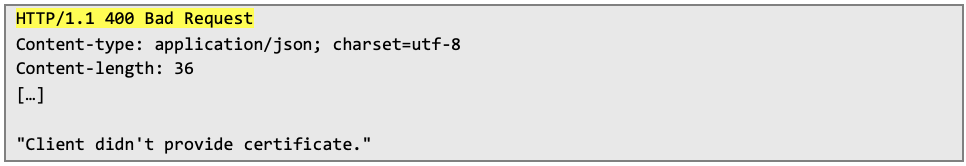 In order to retrieve the certificate, the Objection framework can be used:
In order to retrieve the certificate, the Objection framework can be used:
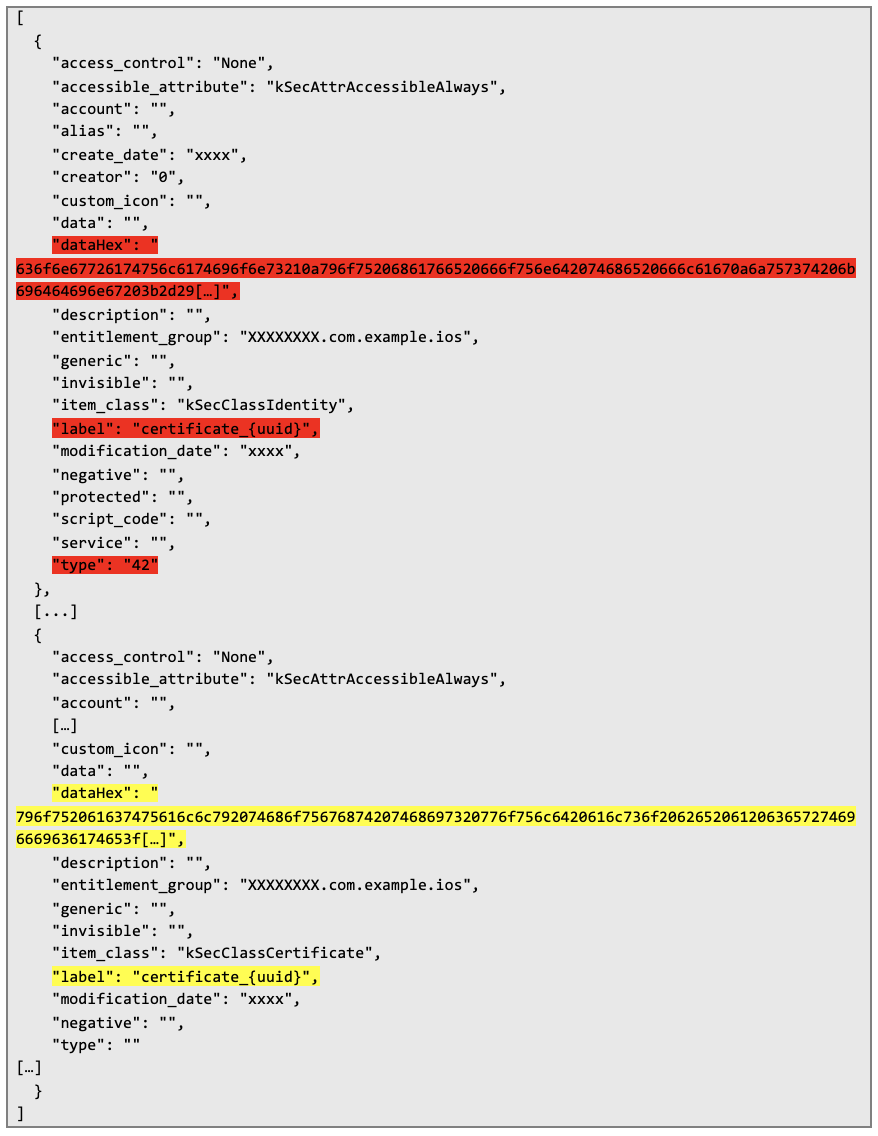
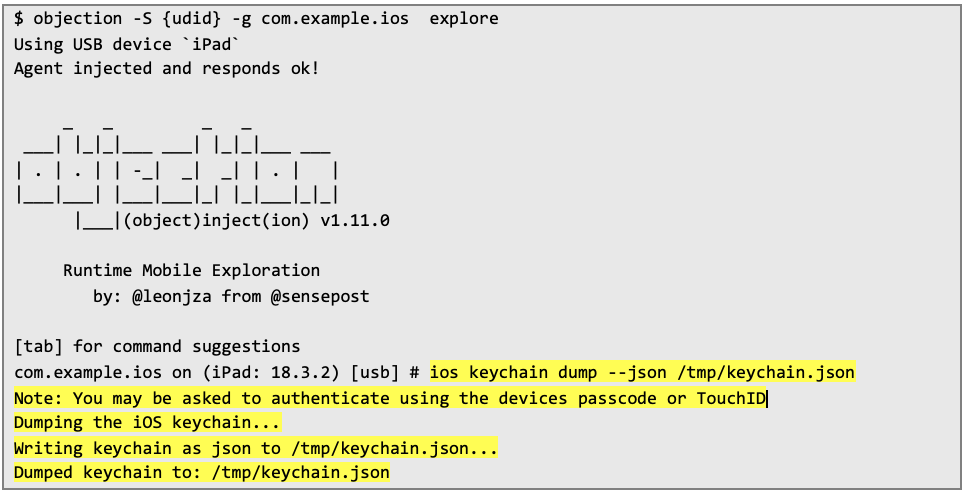 Below there is a dumped keychain file. Certificate is marked yellow and corresponding private key – red:
Below there is a dumped keychain file. Certificate is marked yellow and corresponding private key – red:
 Next, the obtained data must be processed into a format that allows generating a PKCS #12 archive:
Next, the obtained data must be processed into a format that allows generating a PKCS #12 archive:
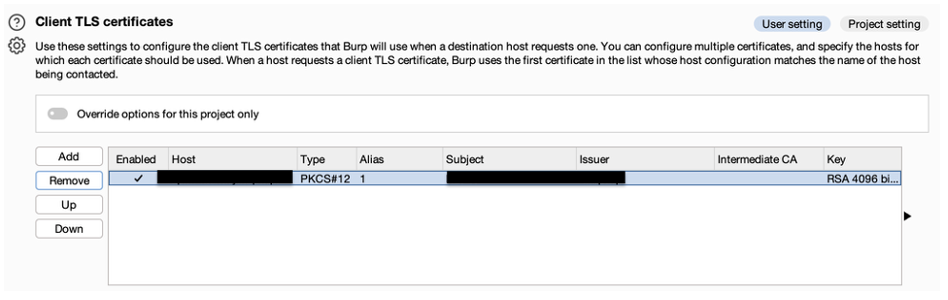
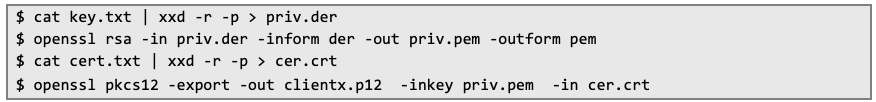 After that action archive can be loaded in the Burp Suite:
After that action archive can be loaded in the Burp Suite:
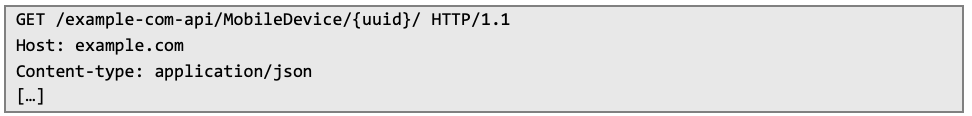
 Now, initial request can be resent:
Now, initial request can be resent:
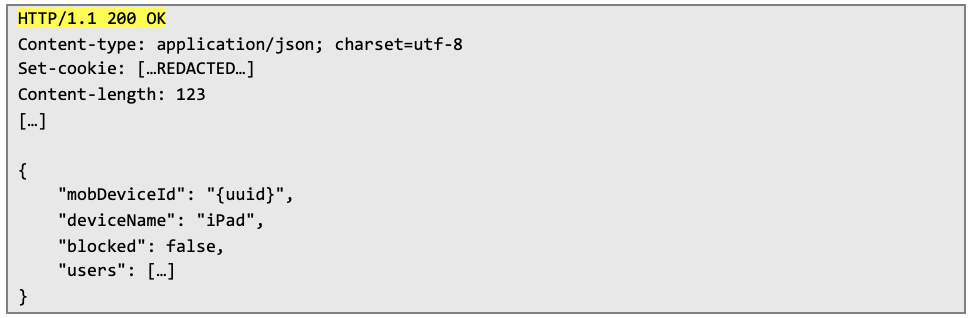
 The server’s response indicates that the operation was successful:
The server’s response indicates that the operation was successful:
 Conclusions and Defensives
While the Keychain provides robust protection under normal conditions, it remains vulnerable in certain scenarios - particularly on jailbroken devices.
Conclusions and Defensives
While the Keychain provides robust protection under normal conditions, it remains vulnerable in certain scenarios - particularly on jailbroken devices. To mitigate the risk of unauthorized access to certificates or private keys, application developers and security teams should rely on 3 most crucial things:
1. Strong implementation jailbreak detection - Disallow running the app on jailbroken iOS devices, or in case where application utilizes certificates degrade app functionality when such dangerous environment is detected.
2. Secure runtime - Harden the application against runtime tampering attempts by blocking dylib injection or monitoring runtime integrity.
3. Apply code obfuscation and anti-tampering measures - Make it harder for attackers to reverse engineer or modify the app.
By combining these defensive strategies, organizations can significantly reduce the risk of private key compromise and unauthorized certificate extraction from the iOS Keychain.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


