
Pentest Chronicles
Bypassing Host Validation:
Real Pentest Case of Sensitive Data Exposure

Mateusz Kowalczyk
October 11, 2024
Environment overview In this case, the vulnerability occurs from how the application handles host validation when sending requests.
The system was designed to whitelist specific domains and reject requests to unapproved external hosts. However, I found that this validation could be bypassed using a special character in the domain name, which allowed unauthorized external communication.
To exploit this vulnerability, we need to have user account in the tested application. The application used different templates, for this vulnerability I used Customer password reset template where (what is important) custom HTML content can be inserted.
Then I inserted an iframe element with a malicious URL into the editor:
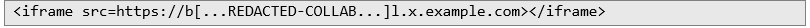
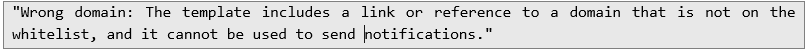
Initially, the application displayed an error message:
 Bypassing Validation However, when we modified the domain by adding special characters, for example $, the application allowed the request to pass:
Bypassing Validation However, when we modified the domain by adding special characters, for example $, the application allowed the request to pass: 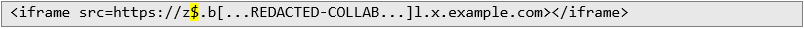 Exploiting the Bypass: I decided to refine the payload by using a special character £, which the application transformed into a valid URL:
Exploiting the Bypass: I decided to refine the payload by using a special character £, which the application transformed into a valid URL:  The application interpreted this as a valid, whitelisted URL:
The application interpreted this as a valid, whitelisted URL: 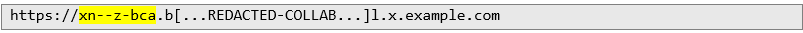 In this case, when the special character £ was included in the domain, the application transformed it using an encoding system called Punycode. Punycode is designed to represent Unicode characters in a format that can be used in the domain name system.
In this case, when the special character £ was included in the domain, the application transformed it using an encoding system called Punycode. Punycode is designed to represent Unicode characters in a format that can be used in the domain name system. As a result, the application transformed the £ into its Punycode equivalent (xn--z-bca), making the URL appear valid according to the host whitelist rules.
Extracting Sensitive Data With the host whitelist bypassed, I was able to demonstrate how this vulnerability could be used to steal sensitive data, such as user password reset tokens. By embedding the following payload:
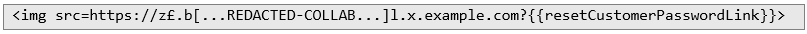 Recommendations To avoid vulnerabilities like this in your applications remember to implement strict validation to ensure special characters and encoded URLs are properly handled and that only trusted domains are allowed.
Recommendations To avoid vulnerabilities like this in your applications remember to implement strict validation to ensure special characters and encoded URLs are properly handled and that only trusted domains are allowed. #CyberSecurity #PentestChronicles #RedTeam #Infosec #DataSecurity #PenetrationTesting #VulnerabilityAssessment
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


